pfSense - Logging to a Remote Syslog Server
In this article we will learn how to send our logs to a remote syslog server. Logging to a remote server has many benefits like the ability to create custom alerts based on syslog entries, the ability to troubleshoot wider issues within our infrastructure and many more.
1) Installing syslog-ng
We will send our log through an IPsec VPN tunnel and the pfSense syslog only worked if I have selected the VPN tunnel interface. This approach is undesired because the logs are send with the VPN tunnel gateway IP and we want our firewall to be seen on the other side of the tunnel by its management IP address instead.
To circumvent this issue we will install syslog-ng and forward our logs locally to syslog-ng that will send the log to the remote server.
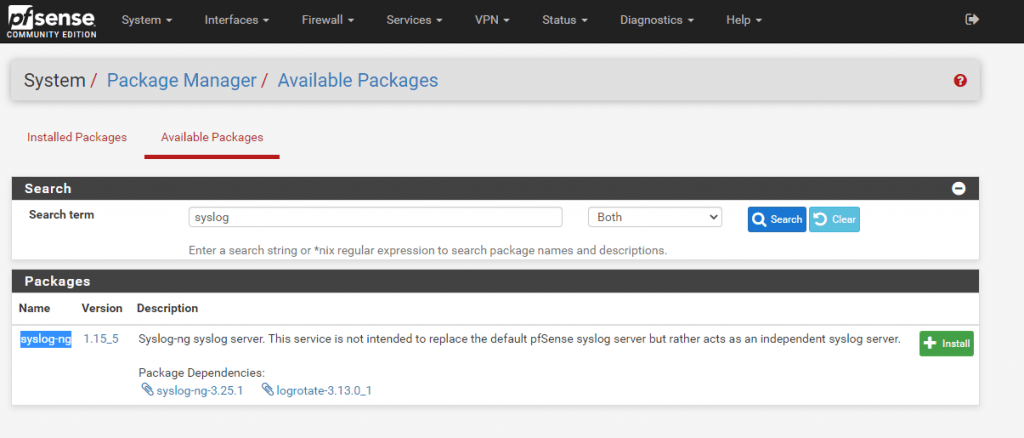
Navigate to System > Package Manager > Avaiable Packages and search for syslog the only result will be the syslog-ng package. Click on the install button to add it to the firewall.

2) Setting syslog-ng
Set the syslog-ng on the GUI as the image below and click on the save button.

3) Send pfSense Logs to syslog-ng
Navigate to Status > System Logs > Settings Tab and at the botton check the Enable Remote Logging checkbox.
Set the settings as the picture below and click the save button.

We are sending all logs to syslog-ng listening on localhost and we should be able to see it receiving the logs under Services > Syslog-ng > Log Viewer Tab as seen on the picture below.
Notice that selecting VLAN4_ROUTERS as the source address the logs will have the source as my management network address which is essential for the remote server.

4) Sending syslog-ng Logs to Remote Server
Syslog-ng is very flexible with its sources and destinations and the next step will be to crate a new destination to connect the local instance to the remote server.
First, we need to add a new destination entry. Navigate to Services > Syslog-ng > Advanced Tab and add a new destination as the picture below.

After, adding the destination we need to connect ir with the remote server adding a new log object as seen below.

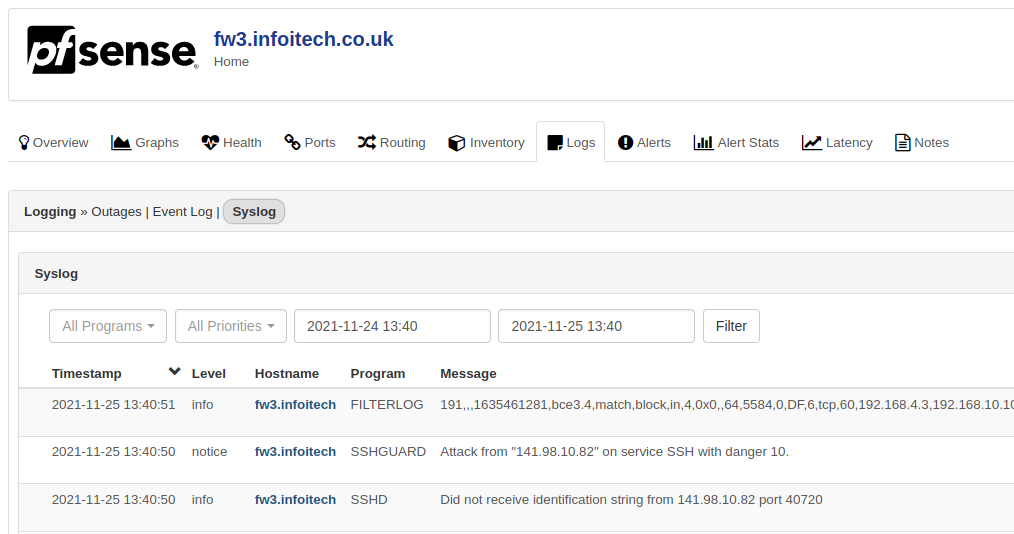
Finally, after saving and if all the firewall holes were added correctly the remote server should be receiving our syslogs.
Conclusion
The steps above guided us into delivering our log to a remote syslog server. However, we are using and insecure connection and the UDP protocol that does not guarantee that our log will be re-delivered if missed on transit. In a next article we will deploy our logs with TLS encryption over TCP. Keep tuned. Thanks for reading my guide.
Resources


![Infoitech - [B]logging](https://blog.infoitech.co.uk/content/images/2021/04/youtube-small-cover-1.png)

