OPNsense(23.7) - Acme Plugin Upload Certificates to Hashicorp Vault

Let's Encrypt certificates are a blessing, no doubt. But they come with an inconvenient fact that they short live—usually, three months. And their rotation is easy if you have just a few around; however, when you have more than ten around your infrastructure, their rotation becomes a problem.
We can use Hashicorp Vault to solve this problem by uploading our certificates to Vault and triggering automation to rotate expired certificates.
This article will cover the creation/renewal of certificates and their upload to Vault. My setup is relatively simple.
- OPNsense creates/renews the certificate using the Acme plugin.
- The Acme plugin uploads the certificates to Vault.
- (In a future article) OPNsense will trigger a GitLab pipeline to rotate the certificates over my infrastructure.
1) Vault - Creating Policies
Before creating a token, we must create the policies it will need.
vault policy write tucana-opnsense-cert-create - <<EOF
# Write permission on 'kv-v2/data/tucana/certs/*' path
path "kv-v2/data/tucana/certs/*" {
capabilities = ["create", "update"]
}
EOF
2) Vault - Generating a Token
With the policy in place, we can create a token for OPNsense.
vault token create /
-no-default-policy /
-orphan /
-type=service /
-policy=tucana-opnsense-cert-create /
-display-name=opnsense-acme-automationKey Value
--- -----
token hvs.zzzzaaaaabbbbcccddddd
token_accessor aaaaabbbcccdddddddsssssrr
token_duration 168h
token_renewable true
token_policies ["tucana-opnsense-cert-write"]
identity_policies []
policies ["tucana-opnsense-cert-write"]3) OPNsense - Acme Plugin Configuration
Here things seemed straightforward forward. Although OPNsense had the option to upload the certs to Vault, the feature was broken, but after a few hours of research and some lines of code changed here and there, I managed to fix it.
Please apply this bugfix before proceeding to the next steps.
An issue was open in github for this problem check if an update was released.
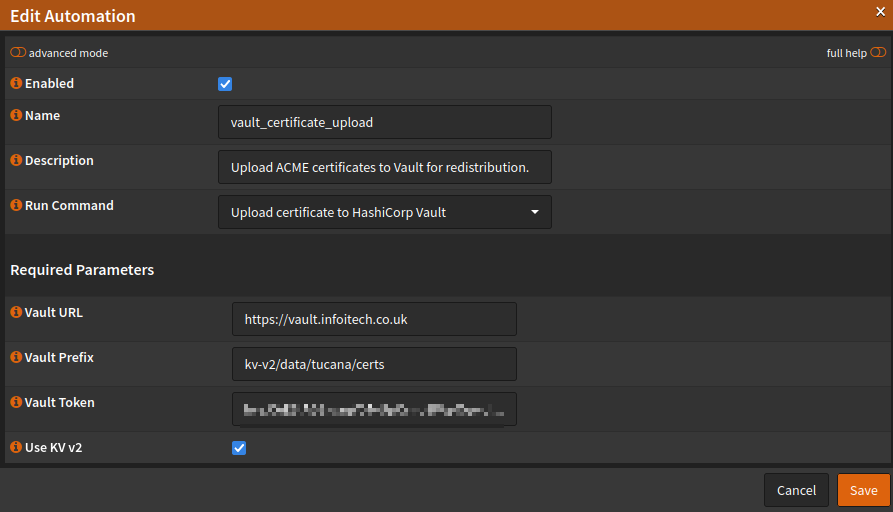
3.1) With the fix applied, navigate to Services>ACME Client>Automations>Add and edit the options as in the picture below, adjusting to reflect your Vault environment.
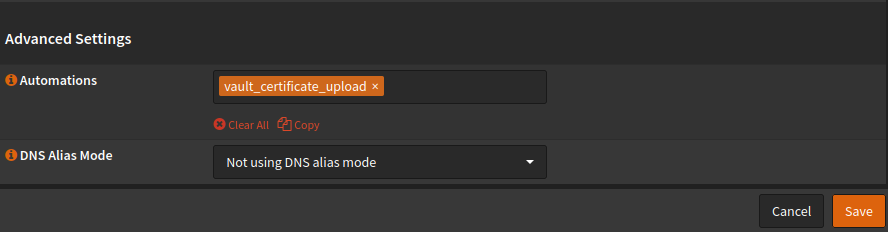
Services>ACME Client>Automations>Add3.2) Navigate to Services>ACME Client>Certificates and set up a new certificate or, as in my case, click the edit button. Under the Advanced Option>Automations, select the previously created automation and save.
Services>ACME Client>Certificates4) Conclusion & Troubleshooting
With the steps above, OPNsense uploads renewed certificates to Vault for redistribution.
If you need to troubleshoot, navigate to Services>ACME Client>Settings and set the Log Level to debug3.
![Infoitech - [B]logging](https://blog.infoitech.co.uk/content/images/2021/04/youtube-small-cover-1.png)

