Cisco CCNA Certification
This article will be used to track the study progress on the Cisco CCNA certificate.
Must Add to the test Sheet
1) Introduction to Networks
1.1) Dissecting Communications

1.2) Network Communications Models
1.2.1) Categorizing Data Transmissions
1.2.2) The OSI Model


1.2.3) TCP/IP vs. OSI Model

1.3) Encapsulation
1.3.1) How Encapsulation works
Segment - chunk of data on the Transport Layer(4)

Packet - chunk of data on the Network Layer(3)
IP Header - From the minimum length of 20 to a total length of 60 bytes

Frame - a chunk of data with a Data Link layer header.
Ethernet Header - contains the MAC address. From the minimum length of 20 to a total length of 60 bytes


Ethernet II Frame - Header Explained
1.4) Data Networks and Addressing
1.4.1) Addressing the Network
Ethernet - uses MAC addresses to address frames.

The first six hexadecimal values are the manufacturer ID and the last six are the serial number of the network interface card.
1.4.2) How Local Communication Works
1.4.3) How Global Addressing Works
Global addressing uses IP addresses.

The tablet will create a frame and encapsulate the packet and send to the router default gateway.
The router will discard the frame analyses the packet and re-encapsulate to send to the internet(next-hop)/upstream gateway.
1.4.4) IP Networks
The subnet mask separates the IP in different networks.

2) Network Layer Addressing and Subnetting
2.1) Introduction to Binary
2.1.1) Binary 101
To count in binary we use place holders and exhaust the possible combinations of zeros and ones.

2.1.2) Converting Binary to Decimal

We just need to multiple the place holder value by itself and add the results.
The binary number above is 192 in decimal.
2.1.3) Converting Decimal to Binary

- First ask the question if it is possible to subtract the number from the place holder value and have left a positive number or 0.
- If yes rinse and repeat.
- Convert the YES to one and the result will be the binary number.
2.1.4) Hexadecimal

To count in hexadecimal we follow the table above.
2.2) Introduction to IP Addressing
2.2.1) What is an IP Address?
An IP address is a unique identifier.
It is composed of 4 octets and each octet contains 8 bits summing a total of 32 bits.

2.2.2) Classless Addressing
IPs are classless and use the network mask to subnet all the available ranges.

2.2.3) Classful Addressing
Classful addresses does not have subnet masks and are divided by classes.

2.2.4) Address Types
There are tree types of address.

Network Address - All bits in the host port are 1.

Broadcast Address: All bits in the host portion are 0.

Host Address: All addresses without zeros and ones in the host portion.
We need to break an address into binary to determine the type of the address.
2.2.5) Private and Public Addresses

2.3) Introduction to IP Subnetting
2.3.1) Framework for Discussing Subnetting
To do subnetting, we must convert the addresses to binary.
2.3.2) Making a Subnet Calculator

This calculator is used to correlate the number of bits in the network mask with the available number of networks and how many hosts each network can have.
2.3.3) Subnetting a Network
Let's subnet the network below into 8 smaller networks.

1) Lookup into the network calculator chart.

2) Set up the problem

3) Calculate Network 0

4) Convert the addresses to decimal.

5) Calculate Network 1


6) Repeat the steps 3 and 4 until the last network.
2.4) Introduction to IPv6
2.4.1) IPv6 Addresses

2.4.2) IPv6 Address Structure
We always keep IPv6 addresses networks at 64 bits long.
- We do not need to but it is highly recommended.
1) We can eliminate leading zeros to shorten an IPv6 Address.

- We can only have one double colon in an IPv6 address.

2.4.3) IPv6 Address Operation
IPv6 operates like IPv4 addresses.
- To use an IPv6 on the internet it has to be a Unicast IPv6 address.
- A different IPv6 address is needed for local communications.

2.4.4) IPv6 Address Types


2.4.5) How Many IPv6 Addresses?



Total of addresses : 340 undecillion, approximately 3.4×1038
2.4.6) IPv6 Static Address
We can static configure IPv6 like IPv4 as seen on the example below.

2.4.7) IP Address Acquision - SLAAC
SLAAC stands for Stateless Address Auto-configuration.
- 1) The router advertises the network it is connected using its link local address.

- 2) The workstation chooses an IP address
Windows creates a random 64 bit identifier to the host.

Unix/Linux/MAC uses a system called Modified EUI - 64
- It is uses the workstation MAC Address and split in two and adds FF:FE
- Take the seventh bit and convert it to the opposite.


- 3) The host sends an Neighbor Advertisement message to the router with the new IPv6 Address
2.4.8) IP Address Acquision - DHCP
The DHCP server on the network can respond to IPv6 addresses requests.
It is recommended to use a DHCP server with IPv6 to allow for easier troubleshooting.
2.5) IPv6 Subnetting
2.5.1) The IPv6 Subnet Mask
IPv6 addresses normally are used in /64 networks which is the recommended.

2.5.2) Subnetting IPv6
Let's use an ISP as an subnetting example. The ISP has a /32 subnet and want to provision 5 customers with a /48 subnet.



2.5.3) Subnetting IPv6 /48
With the /48 the customer will now distribute the address within 5 physical locations in a way that each site can have 256 /64 networks.


- 1) Let's convert the 16 bits available for subnetting into binary, and move every 4 bits

Breaking the subnet every for bits allows easy subnetting, since it is only a matter of count in hexadecimal.

Keep counting in binary to determine the amount of /64 subnets each of the above subnets can accommodate.


The table above tells that each site needs a /56 subnet.
- 2) Counting the hexadecimal each network can be defined.


2.5.4) Subnetting IPv6 /56
London will subnet their /56 into the 5 office locations below.

There are 8 bits to work on the /56 subnet provided as seen on the pink highlighted area.

Keep counting and the subnets for each location should be like below.

2.6) Router Operation
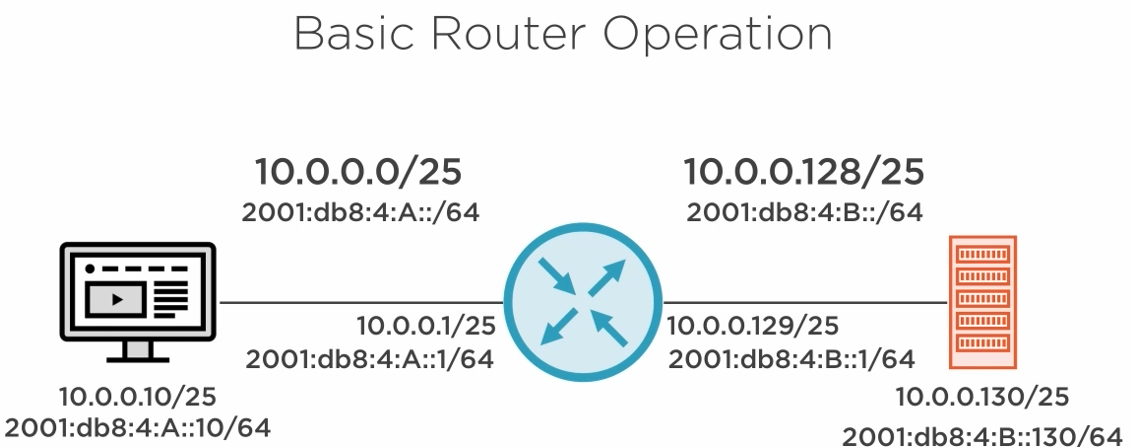
2.6.1) Basic Router Operation


Let's examine a ping message going from host to server.
- 1) The ping message is encapsulated into an IP packet.

- 2) The packet is encapsulated into a L2 frame. With the source MAC Address of the host and destination the router gateway.

- 3) The router receives the frame, discards it.
- 4) Looks the IP destination in its routing table and finds it on the interface in the subnet 10.0.0.128/25.

- 5) It generates a new frame and forward it to the server.

- 6) The server then extract the packet, discard the frame and reads the payload in the packet. The payload contains the ping request and the server respond.
The response follows the same steps above.
2.7) Variable Lenght Subnet Masking
2.7.1) The Need for VLSM

13 Networks will be needed to accommodate the diagram above.

The ISP provides, a /21 subnet to be subdivided into smaller networks.
2.7.2) Setting up the VLSM Problem
The first step is to set up a list with the networks as seen below.

We need to use our Network Calculator to from step 2.3.2 to fill the table with the number of bits needed for each network as seen below.

2.7.3) Calculating Your Networks
Let's calculate the first subnet.
1) Add a divider on the 21 bits provided by the ISP.
2) Set the 9 bits on the host portion as defined on the step above. It gives the netmask of the subnet.
3) Calculate the Network address, First Usable Address, Broadcast Address and Last Usable Address in as seen on the table below.

Repeat the steps above incrementing the networks until the table is completed as below.

Let's calculate the networks for the example below.

The table below show the needed networks.

The result is the on the table below.

3) Ethernet Ops & Switch Config
3.1) Physical Layer Technologies
3.1.1) Twisted Pair Cabling
Twisted pair cable categories.

Cat6 cables have better insulation to prevent noise on the copper pairs.

Shielded cabling is used when running cables along devices that create EFM like fluorescent lights.
3.1.2) RJ-45 Connectors & Cable Types
The diagram below describes both wiring standards.

Crossover cables are used to devices of the same type.
Modern network cards automatically detects the type of cable.


Other types of cables.


3.1.3) Fibre Optics
Fibre optics types.



3.1.4) Wireless Ethernet(802.11)

The electrical magnetic spectrum is divided into channels. A range of frequencies used to transmit information.




3.2) Data Link Layer Technologies
3.2.1) Ethernet
Ethernet is one of the most used protocols used in networking today. It is one of the Layer 2 protocols responsible to move frames/packets around the network.
IEEE 802.3, also known as the Ethernet standard, is a set of standards and protocols defined by the Institute of Electrical and Electronics Engineers (IEEE) that specify the physical and media access control (MAC) aspects of the data link layer for wired Ethernet networks.
IEEE 802.3 has evolved over time to support various types of media, including twisted pair cables (10BASE-T, 100BASE-TX, etc.), coaxial cables (10BASE-2), and fiber optic cables (10BASE-F), enabling Ethernet to adapt to different network environments and requirements
| Media Type | Standard | Speed | Cable Type | Maximum Distance |
|---|---|---|---|---|
| Twisted Pair | 10Base-T (IEEE 802.3) | 10 Mbps | Category 3 UTP | Up to 100 meters |
| Twisted Pair | 100Base-TX (IEEE 802.3u) | 100 Mbps | Category 5, 5E, or 6 UTP | Up to 100 meters |
| Optical Fiber | 100Base-FX (IEEE 802.3u) | 100 Mbps | Multi-mode | Up to 412 meters |
| Copper Twisted-Pair | 1000Base-CX (IEEE 802.3z) | 1 Gbps | Category 5 UTP | Up to 25 meters |
| Copper Twisted-Pair | 1000Base-T (IEEE 802.3ab) | 1 Gbps | Category 5 UTP | Up to 100 meters |
| Multimode Fiber | 1000Base-SX (IEEE 802.3z) | 1 Gbps | Multimode Fiber | Depends on the specific fiber type |
| Single-Mode Fiber | 1000Base-LX (IEEE 802.3z) | 1 Gbps | Single-mode Fiber | Depends on the specific fiber type |
| Twisted Pair | 10GBase-T (802.3an) | 10 Gbps | Category 5e, 6, and 7 UTP | Up to 100 meters |
3.2.2) Wireless
The wireless Ethernet protocols are also controlled by IEEE and has evolved over the years as seen on the table below.






3.2.3) Other Data Link Layer Protocols

3.2.4) Serial Communication Protocols

3.3) Introduction to Ethernet
3.3.1) A Brief History of Ethernet


3.3.2) CSMA/CD

This is a bus network and collisions are a voltage spike on the wire.

3.3.3) Duplex and Speed




3.3.4) Ethernet II Frame

A frame encapsulates a Layer 3 packet.

Each has its own max number of bits allowed.

The destination MAC address consists of several pieces. Manufactures have an ID provided by the IEEE when they purchase an Ethernet license. This ID are the first 24 bits and the other 24 bits is an unique number.
3.4) Introduction to Ethernet
3.4.1) Network Topologies

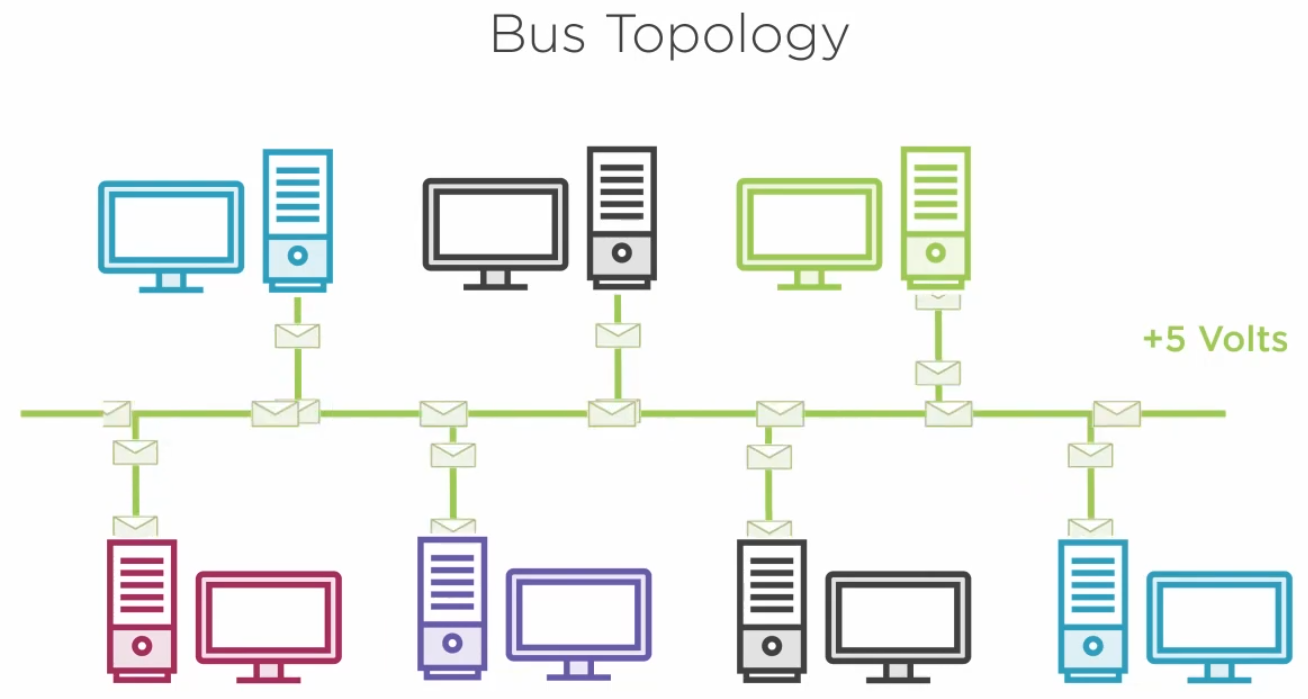
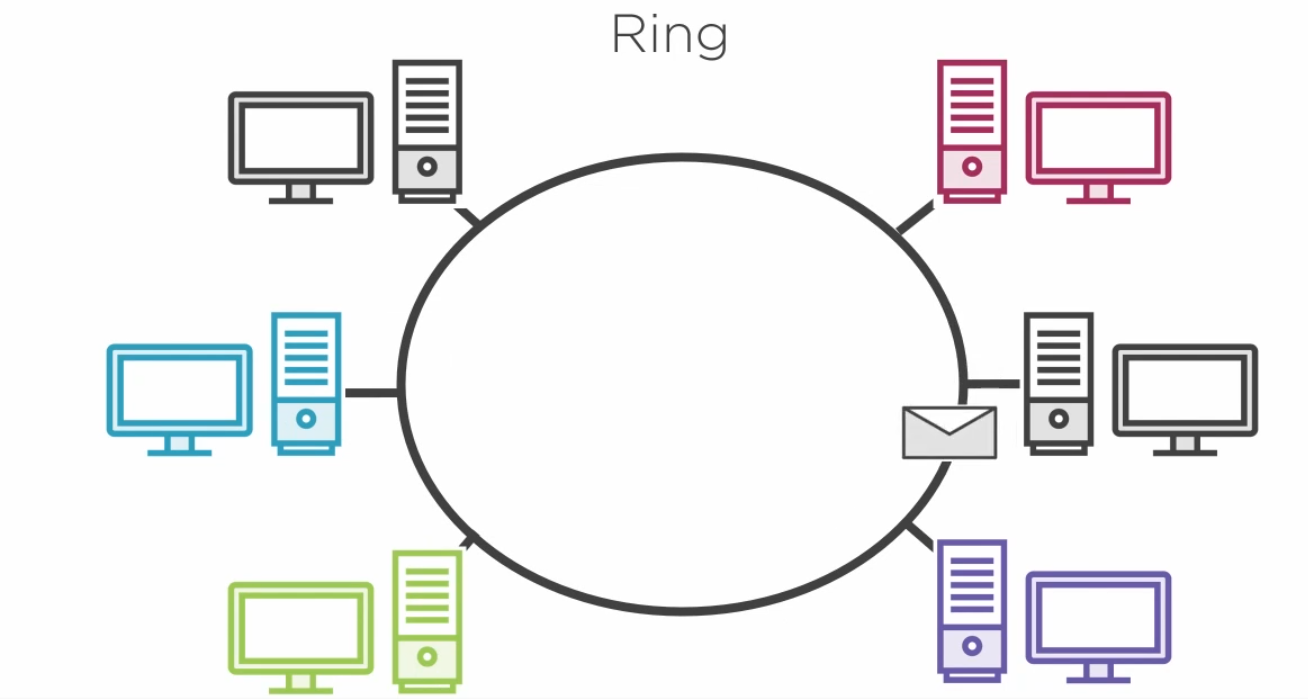
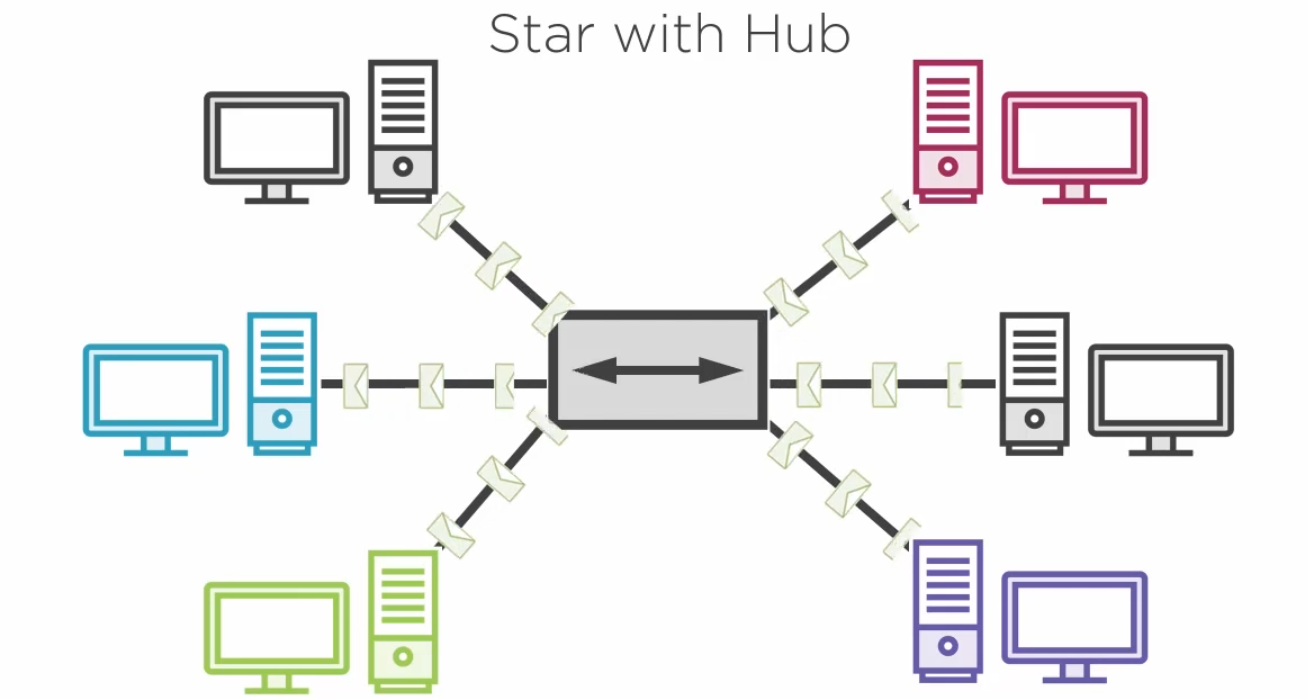

3.4.2) The Mac Address Table
The layer 2 switch does not have issues with collisions because it keeps track of the MAC address of each device connected to it.
The switch then switches the circuit between devices talking on the network.
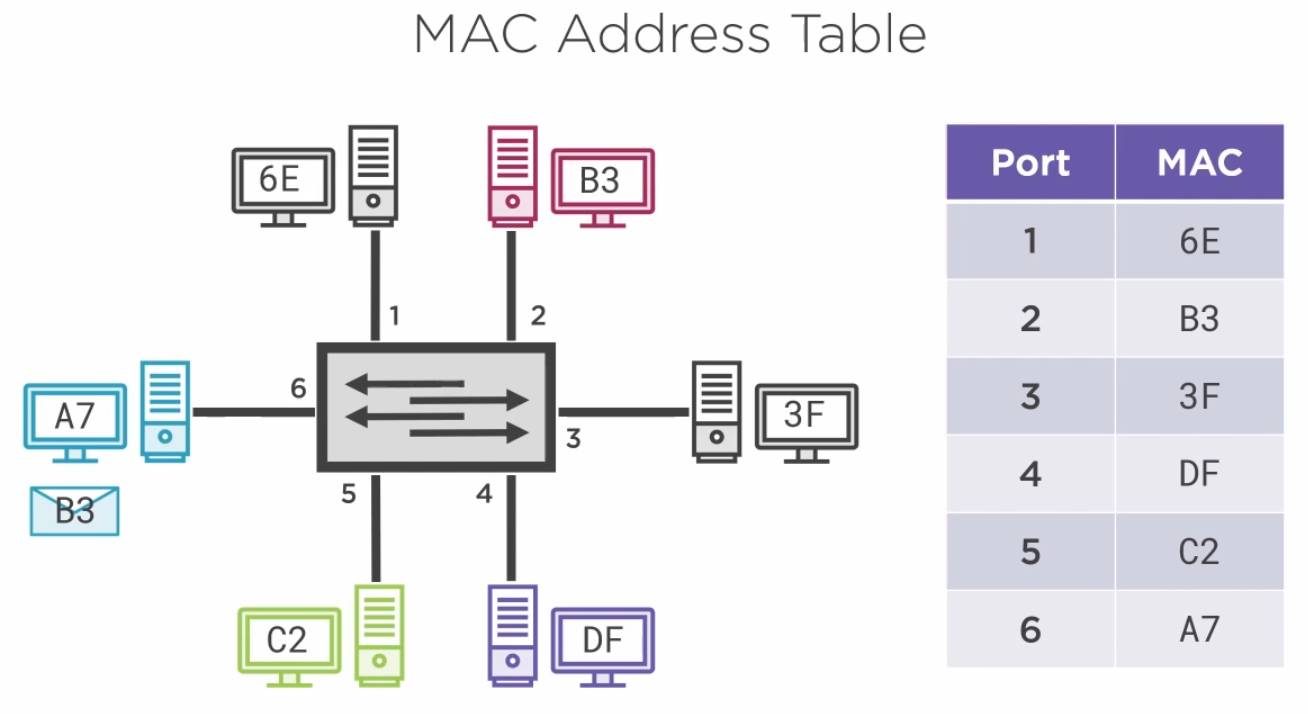
3.4.3) Broadcast and Broadcast Domain
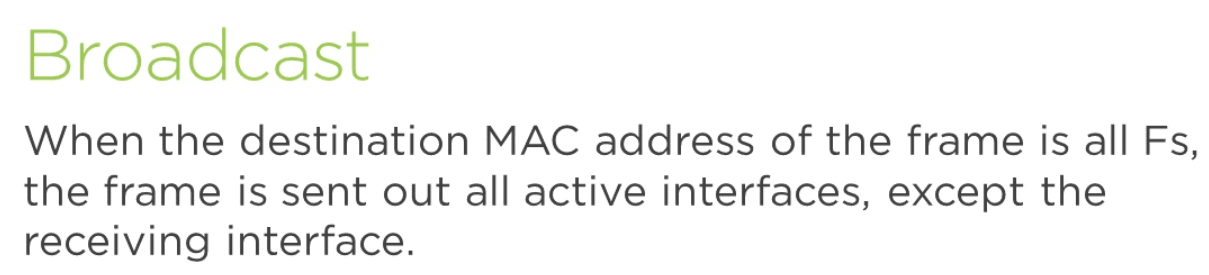
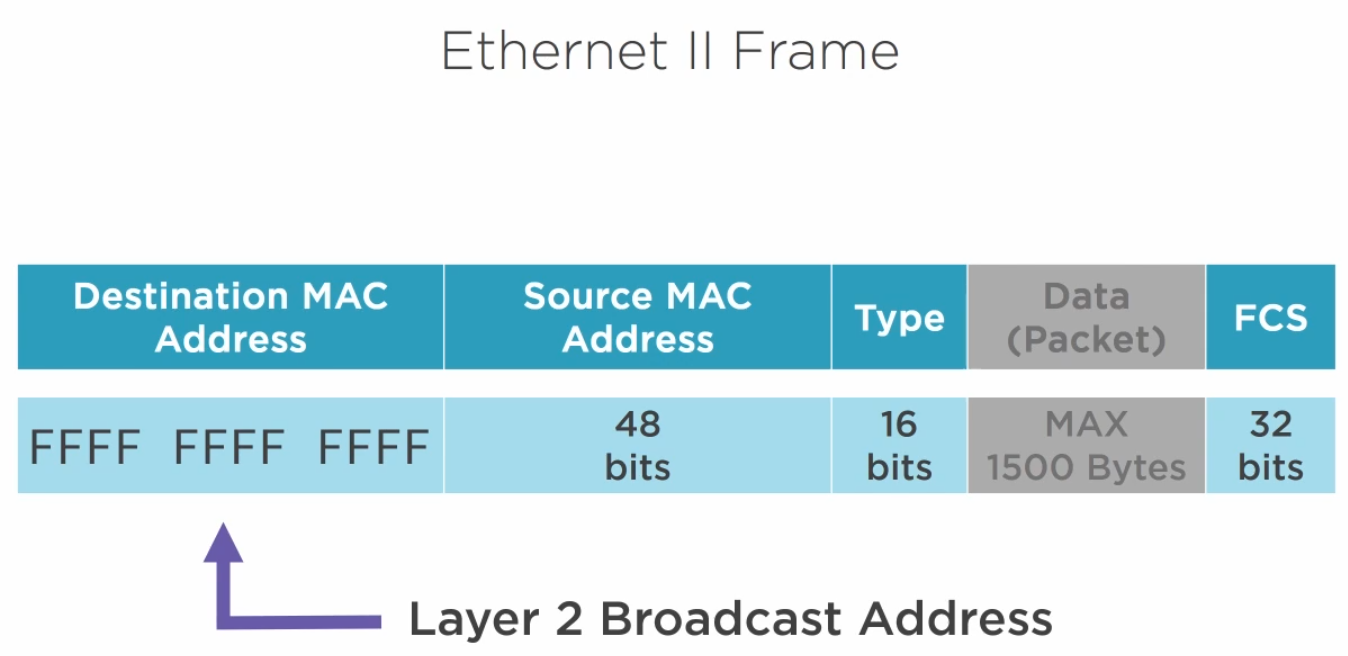

A switch breaks out a collision domain whilst a router breaks out a broadcast domain.
3.4.4) Examining MAC Address Table
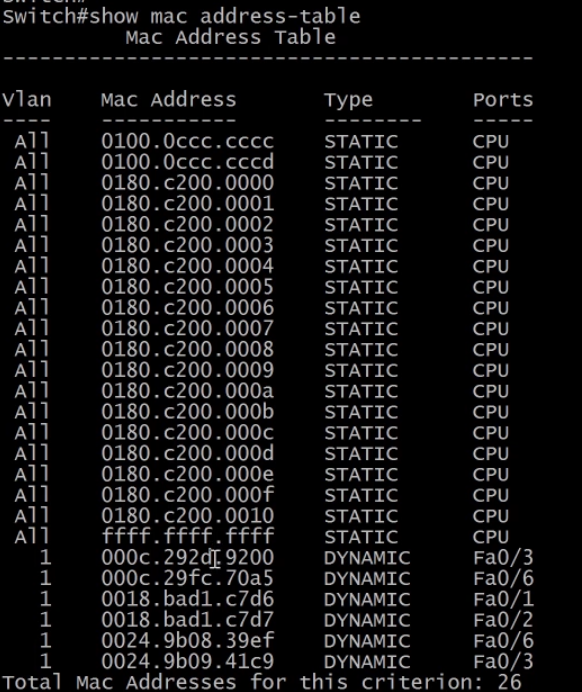
The command used to show the MAC address table is show mac address-table on Cisco devices.
3.4.5) Cascading Switches
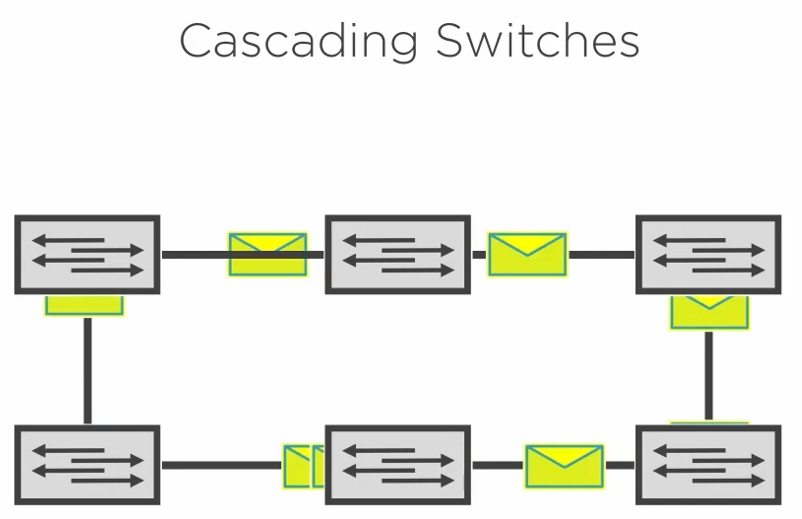
When cascading switches we need to be careful with broadcast traffic. It can create a loop on the network or broadcast storm.
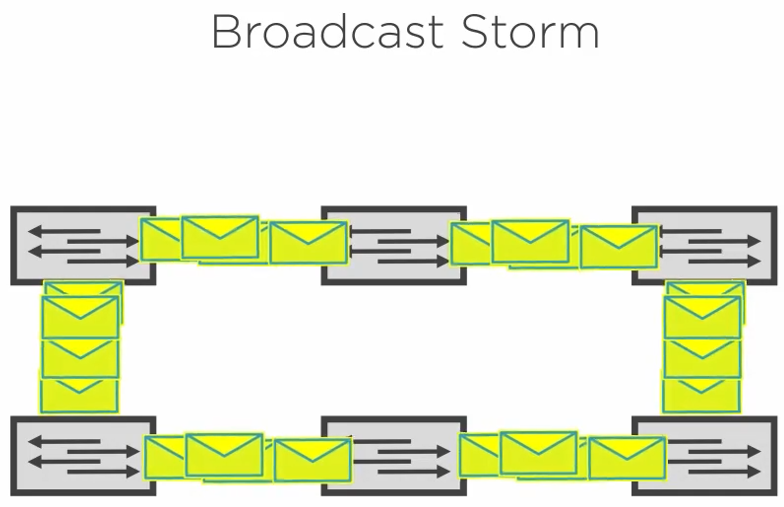
A broadcast storm will eventually crash the network.
3.5) Switch Configuration
3.5.1) Switch Memory and Lab Config
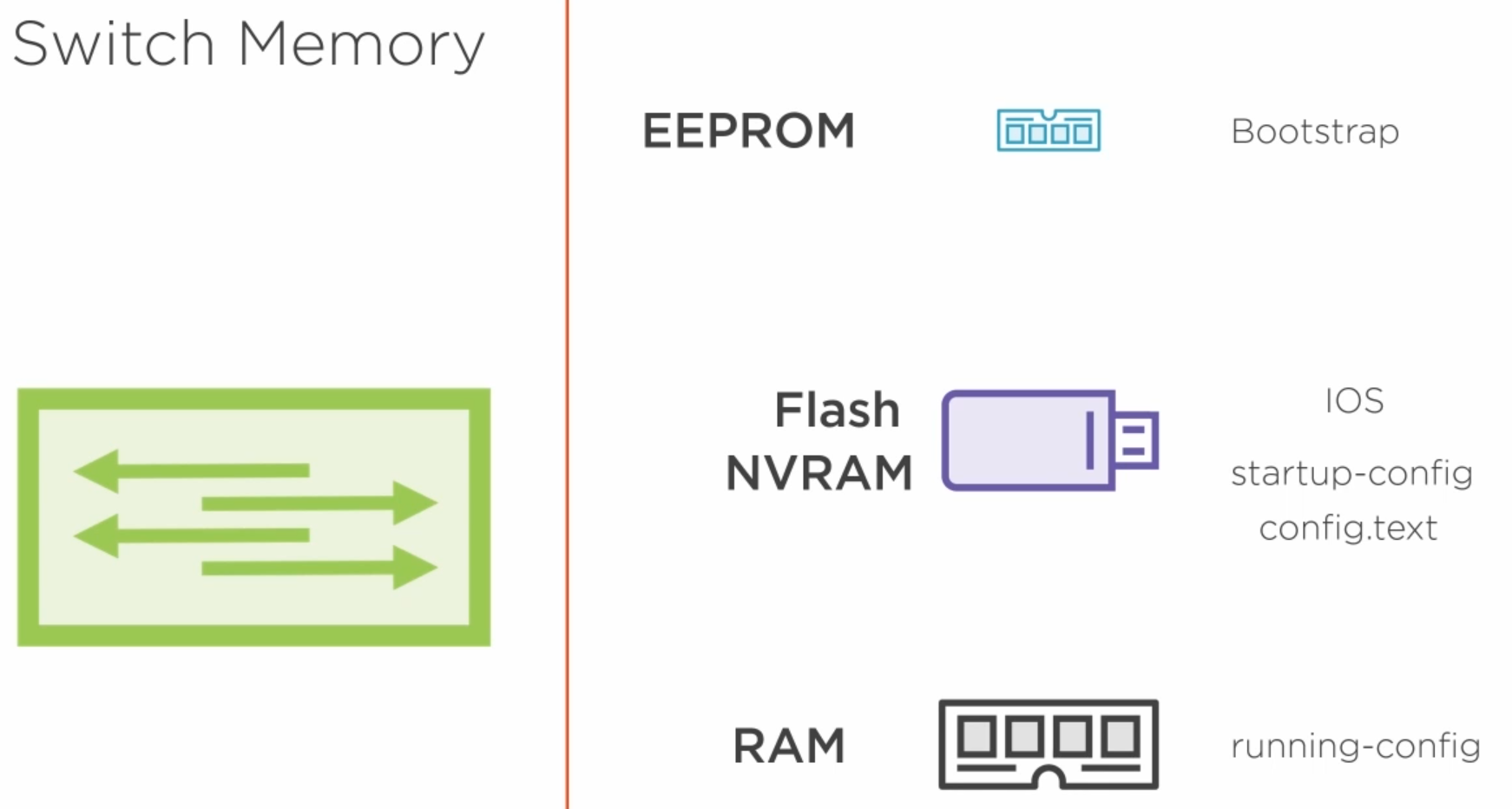
The switch bootstrap is stored on EEPROM which is the operating system to load the IOS.
The IOS image is stored in Flash memory like in a router.
The start-up config is stored in NVRAM except that it is actually a virtual device created in Flash.
The running-config is stored in RAM.
When the command to copy the running-config to the startup-config which is stored in the NRAM as config.text that is an alias of startup-config.
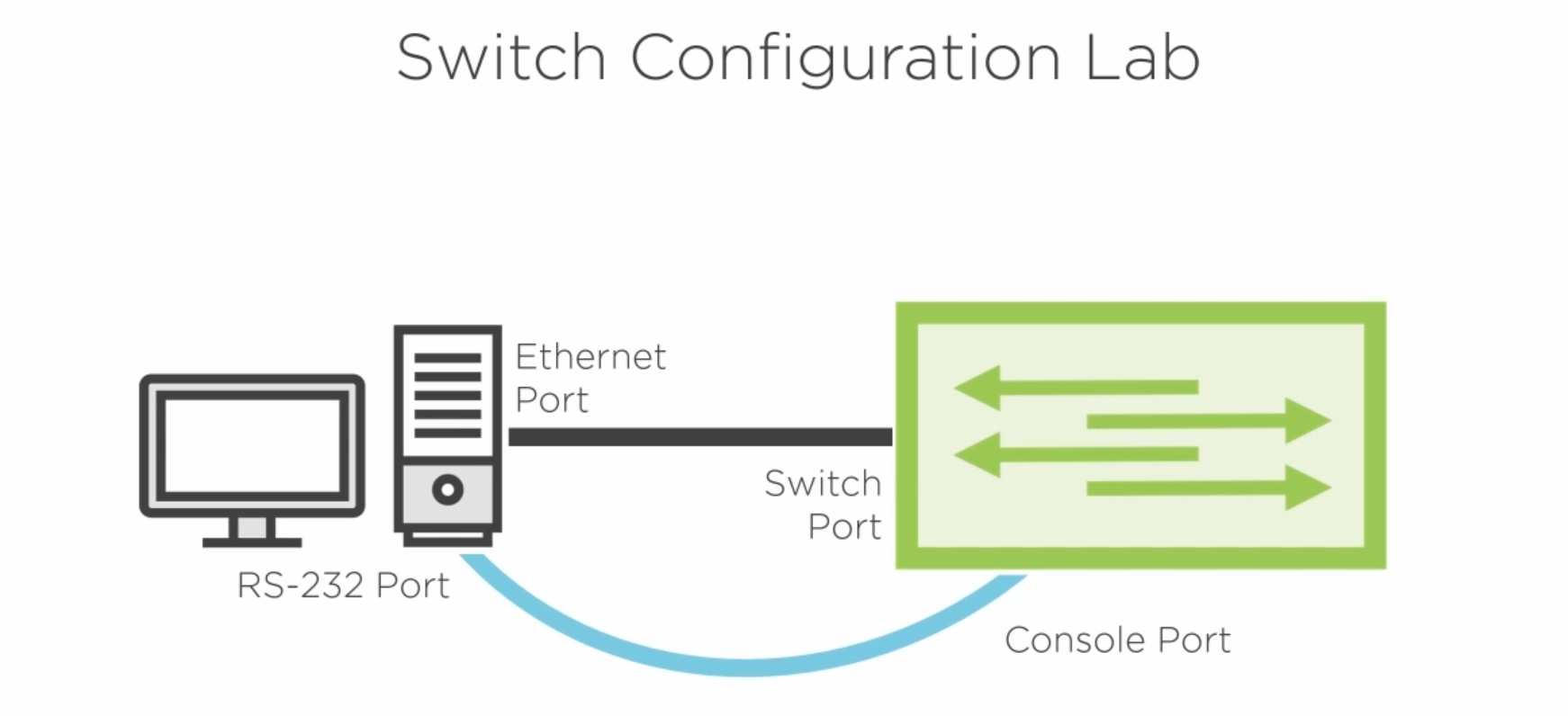
The lab setup diagram is below.
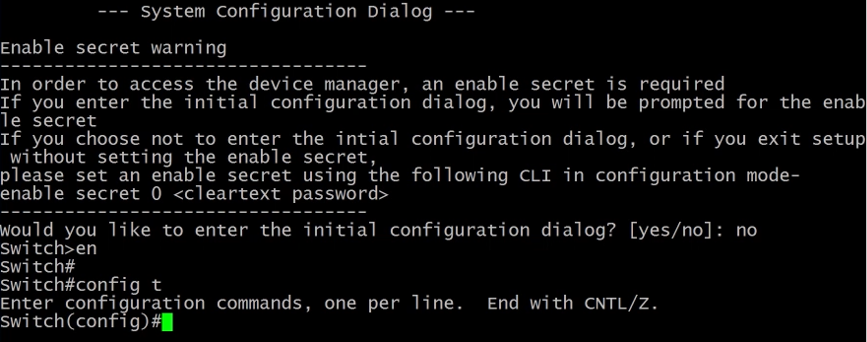
3.5.2) Switch Configuration with SSH
hostname> - the switch or router is in user mode. The greater (>) sign indicates the mode.
- The
enablecommand moves you to proviprivilegedeged mode.
hostname# - privilegde mode.
- The
config terminalwill take you to configuration mode.
hostname(config) - configuration mode.
hostname <hostname> - command to change the device hostname.
ip domain-name <domain_name> - command to change the domain name that is required to generate an SSH key.
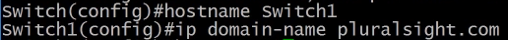
banner motd #<message># - sets the message to be displayed when a new session is initiated.
enable secret <password> - command used to set the router root password.
username <username> secret <password> - A new user should be created to allow SSH access.
crypto key generate rsa - generate a new crypto key to allow SSH key authentication.
- This command will ask for the number of bits in the mask, using 1024 as the minimum.
- It will also enable SSH v1.
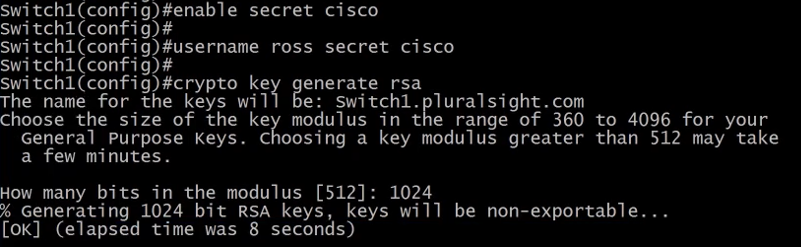
ip ssh ver 2 - use this command to enable SSH V2.
service password-encryption - encrypt all plain text passwords in the configuration.
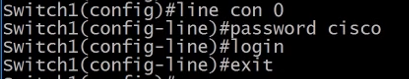
line con 0 - to configure the console port.
logging sync - to avoid disruptive messages whilst entering commands.
password <pasword> - set a password to console access.
login - forces the user to enter credentials to serial connect to the router.
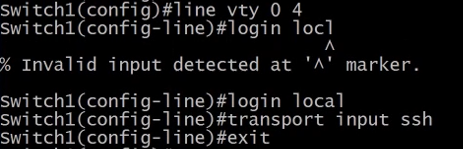
line vty 0 4 - limit the number of SSH connections to the switch/router.
login local - tells the switch/router to use the local user database.
transport input ssh - to only allow SSH.
The switch needs an IP address to allow SSH connection and to set an IP address a VLAN is needed.
interface vlan 1 - creates a virtual interface. This interface is called SVI (Switched Virtual Interface).
- All physical interfaces by default are in
no shutdownand are part of VLAN 1.
It is an interface on the switch that has a MAC Address and can have an IP address set.
no shutdown - is used to enable a port that by default is turned off.
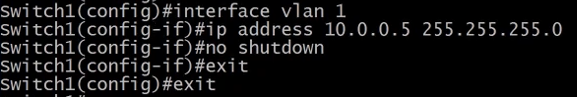
show running-config - shows the running configuration.
copy running-config starttup-config - to save the config in memory to the flash memory.
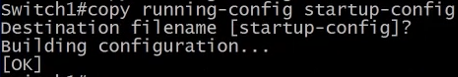
show flash: - show the files on the switch flash. And the config.text is the startup-config.
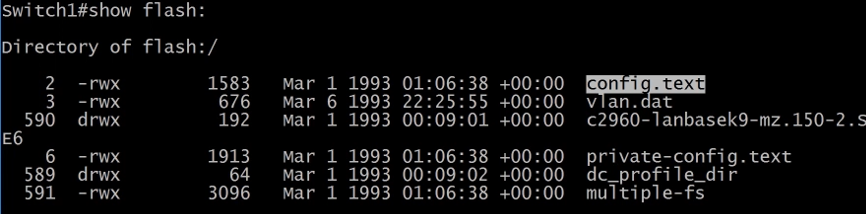
3.5.3) Resetting a Password on a Switch
Press the only button on the front of the switch until it boots up. When you release the button it will take you to the switch ROM monitor mode.
flash_init - command used to initilise the switch disk.
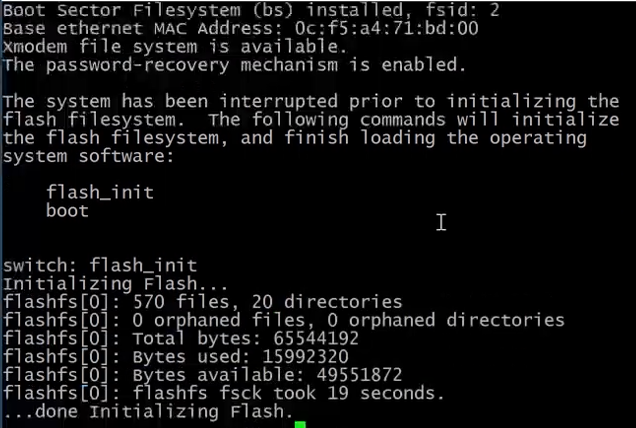
dir flash: - this command will show the flash files.
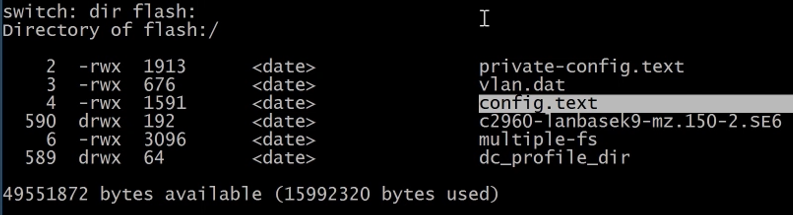
The config.text contains the startup-config with the unknown password. Let's rename the file to config.bak . If the configuration is not needed the file can be deleted with the delete command.
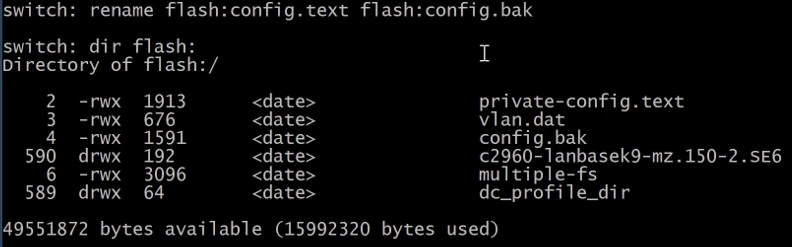
boot - this command in ROM monitor mode reboots the switch.
After the reboot the switch has the default configuration loaded. We can now rename our config.bak file back to config.text .
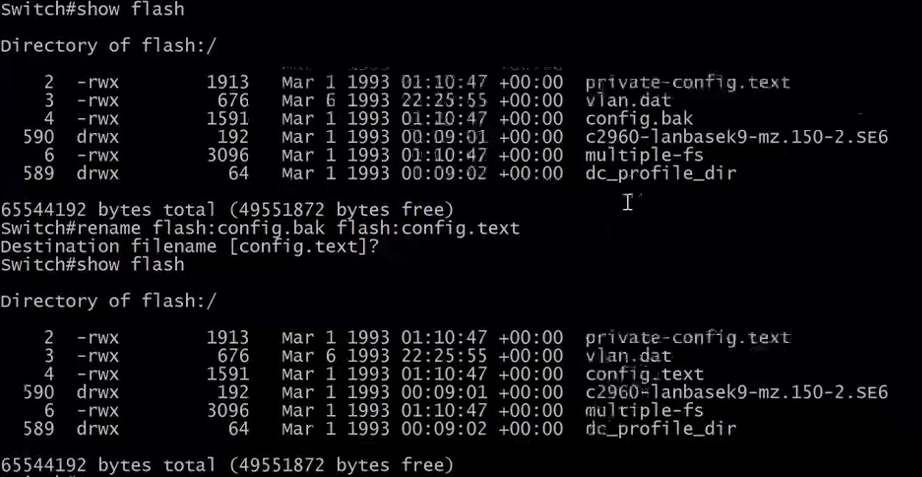
We now need to copy the startup-config to the running-config.
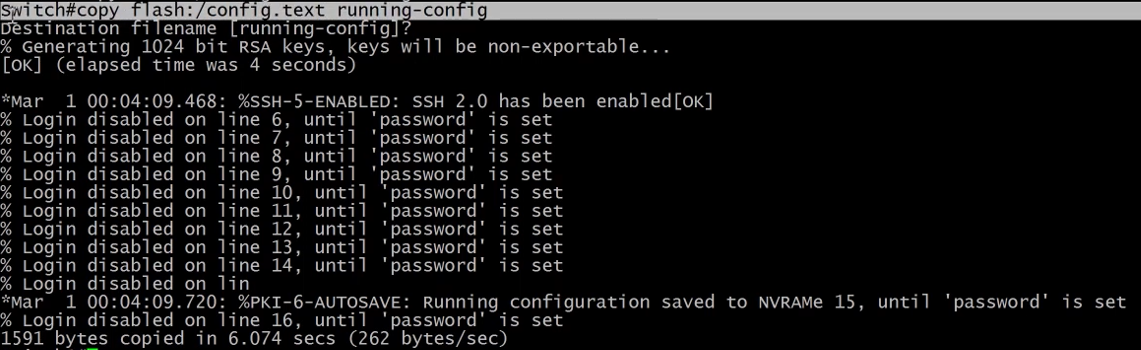
After the config is copied, we can go into configuration mode and issue the command enable secret <password> to set a new password.
Finally, copy the running-config to the startup-config to save the new password.
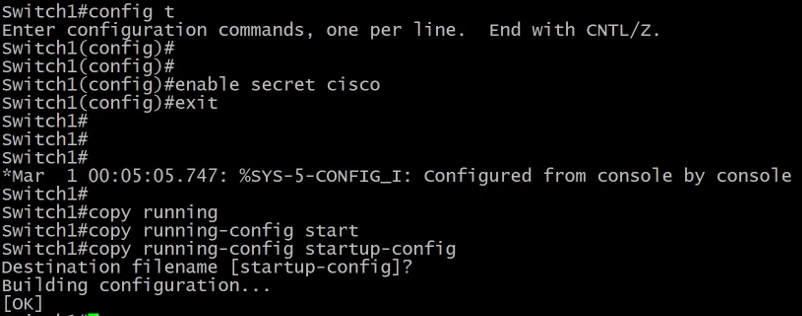
3.5.4) Upgrading the IOS on a Switch
Let's first check the version running with the command show version
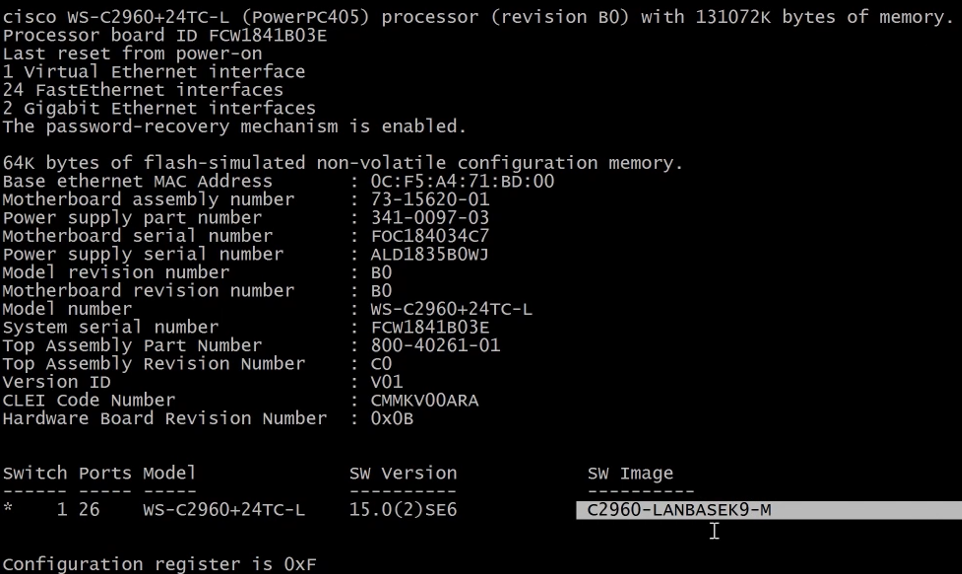
c2960-LANBASEK9-M - is the image version running.
15.0(2)SE6 - is the IOS version running.
To find the image being loaded during the boot we need to inspect the flash as seen below.
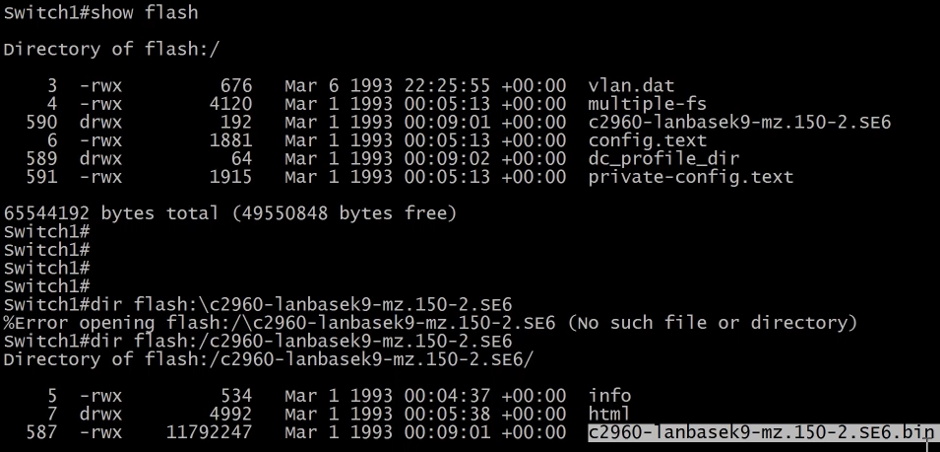
Before uploading an image to the switch we need to check if there is enough space. In our case, the new IOS image has 11Mb.
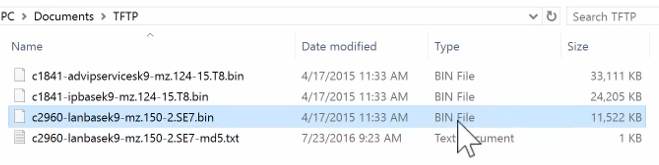
The show flash command shows the amount of space available.
We will transfer the file using Tftp. Let's enable the server on our computer.
And now on the switch, we can issue the command below to copy the new image.
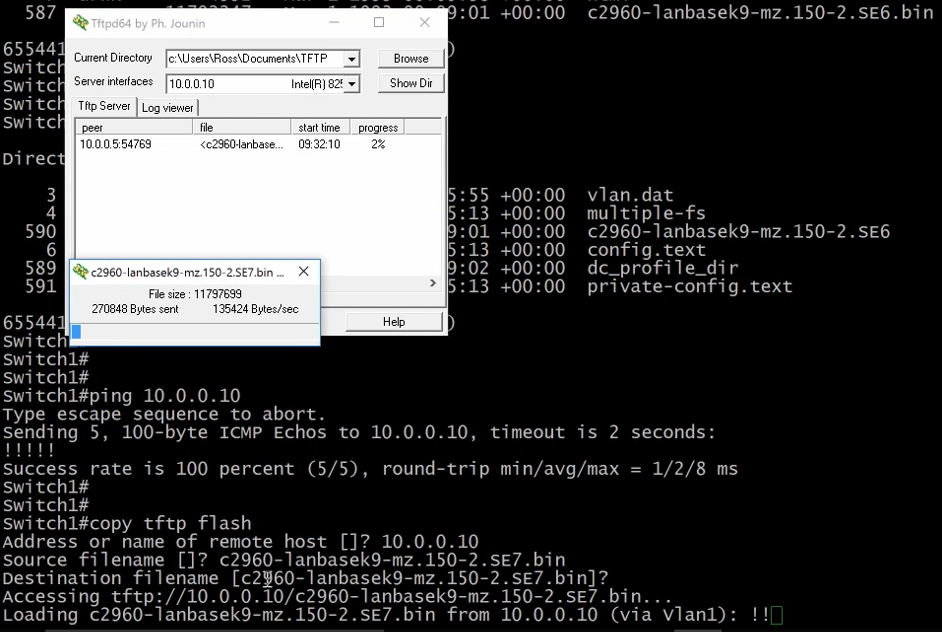
We can now show the flash contents to confirm the file was transferred.
Before using the image, we should check if the file is not corrupted with the md5 utility. When the file is downloaded from Cisco the MD5 will be provided.
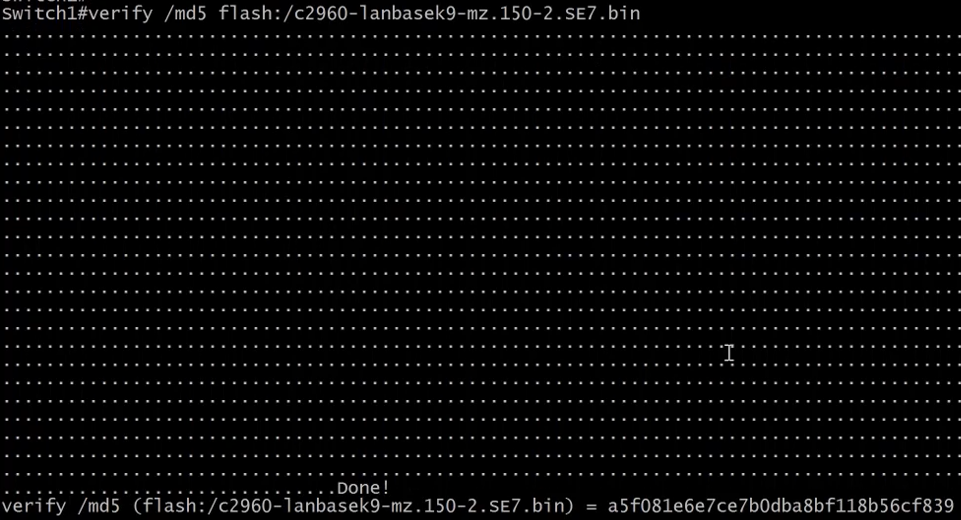
We can now tell the switch to use the new image file to boot.
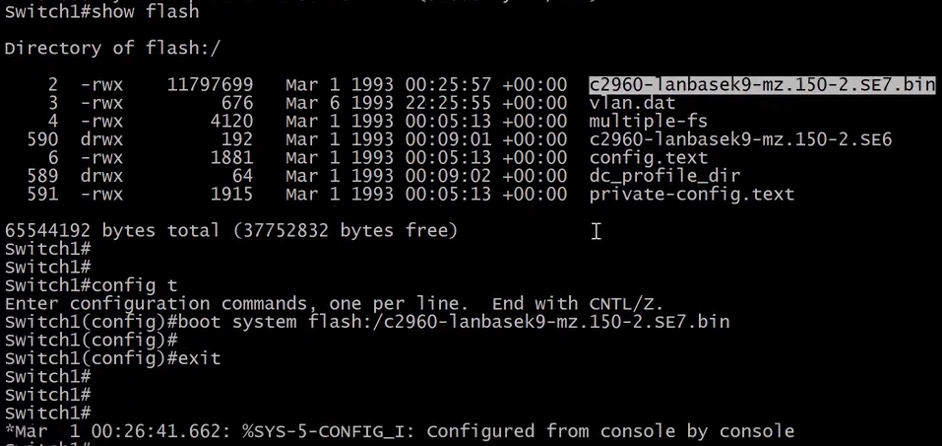
And finally, copy running-config startup-config issue the reload command to reboot the switch.
With the show version command we can verify if the IOS version has been updated.
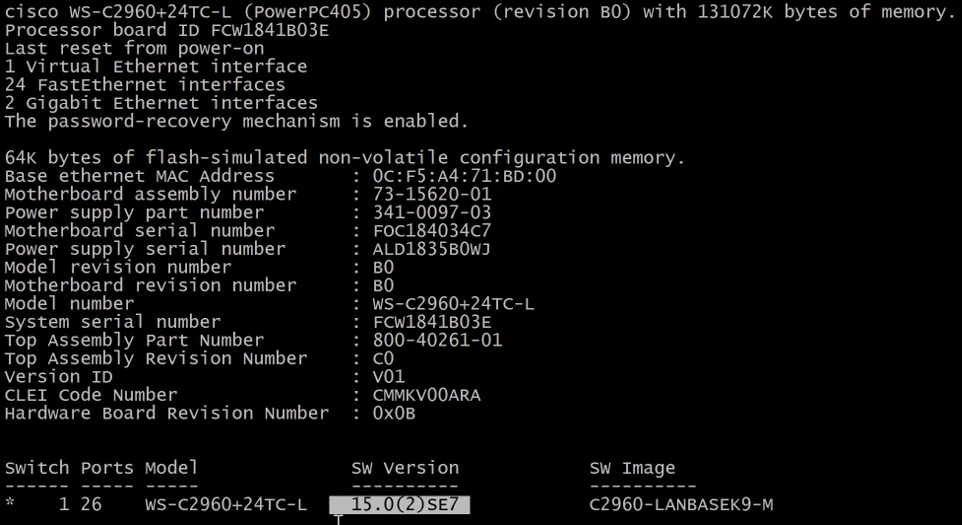
3.5.6) Reading Mac Address Table
To inspect the MAC address table or CAN (Content Address Table).
show mac address-table - will show the whole MAC table.
show mac address-table dynamic - only shows dynamic MACs.
show mac address-table interface <interface_name> - show the MAC address learned on an interface.
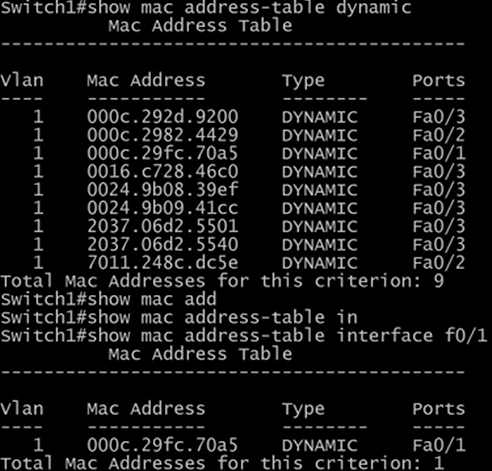
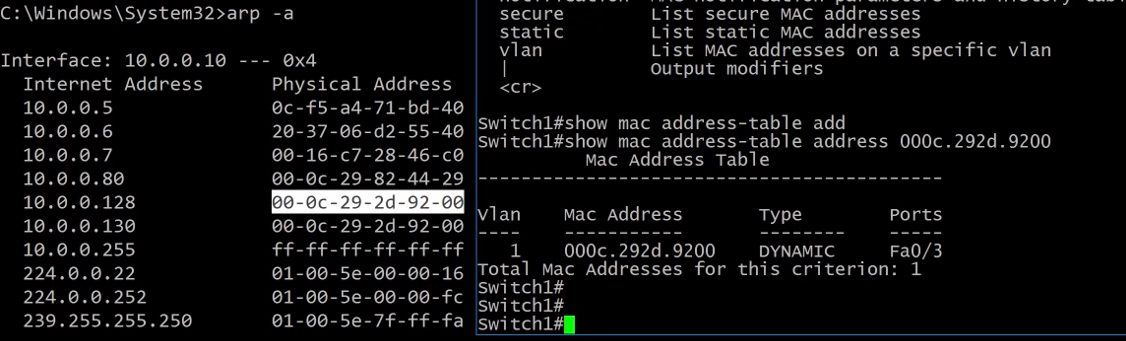
We can also pass a MAC Address to the show mac command and it will return the port it's been learned.
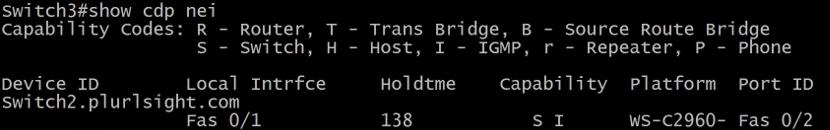
Another command that can be used is the show cdp neighbourthis command will tell if there is another Cisco switch directly connected.
4) Configuring a Cisco Router
4.1) Cisco Router Basics
4.1.1) Cisco Router Components
Data communication ports are used to move data between networks.

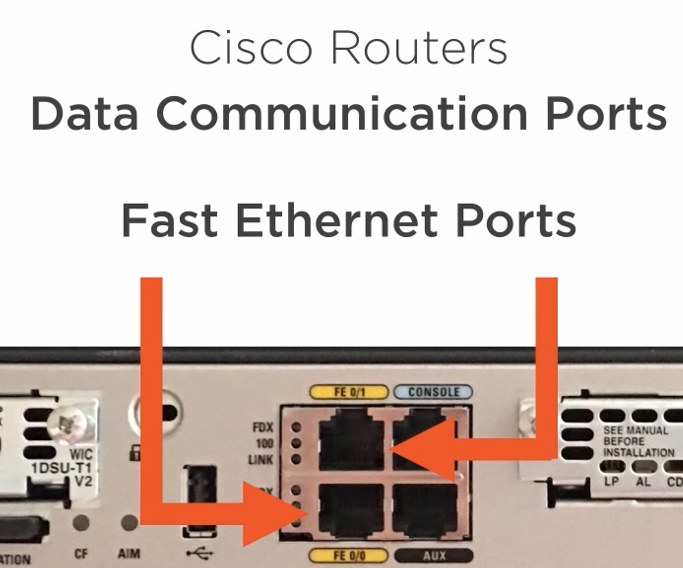
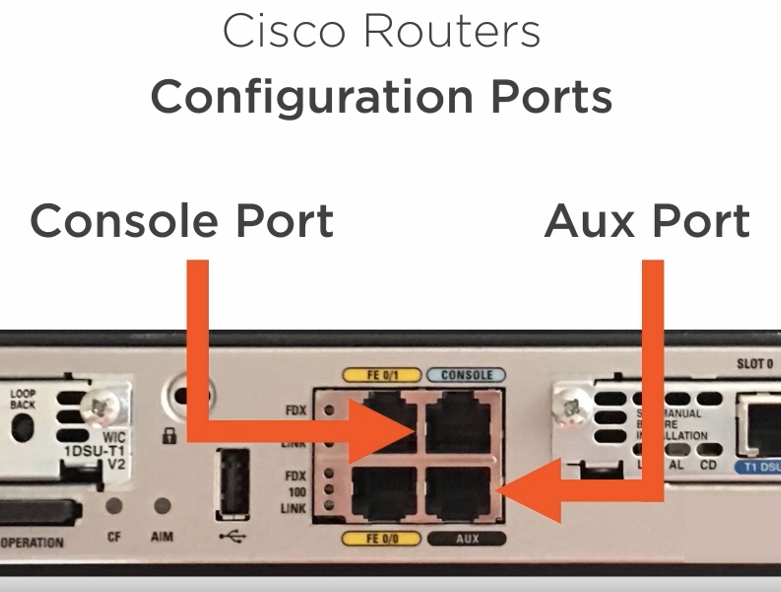
4.1.2) The Router Boot Process
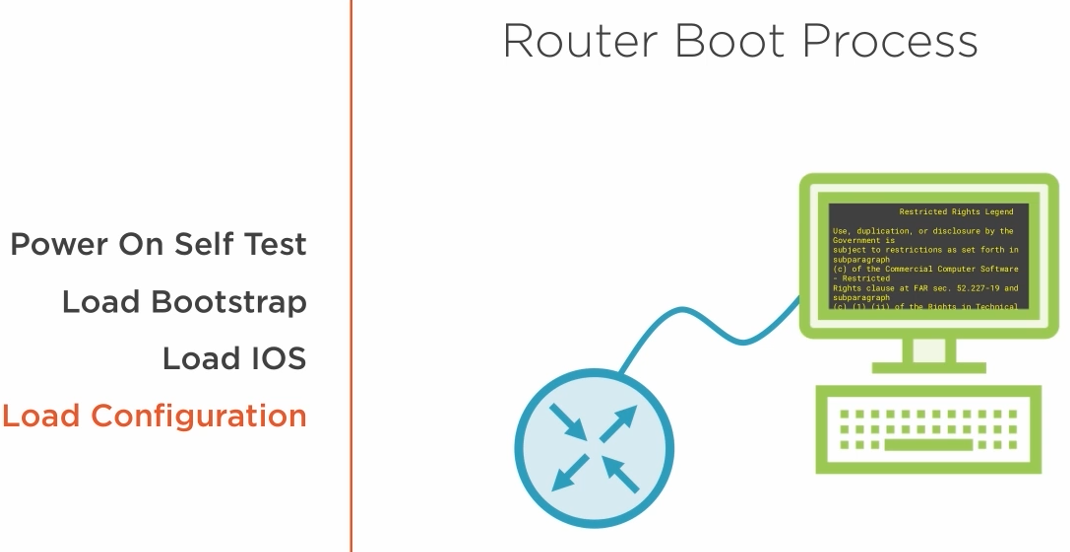
1) The Router loads the bootstrap, which is equivalent to the BIOS of a PC.
2) The bootstrap then loads the IOS.
3) The configuration file is loaded.
4.2) Cisco Router Files and Licensing
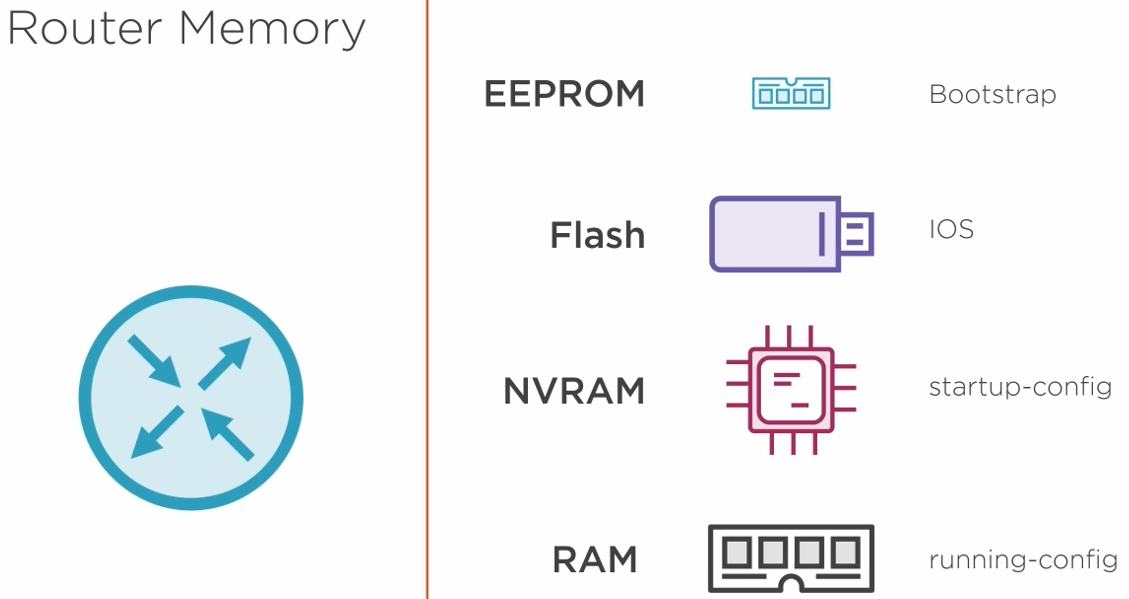
4.2.1) Router Memory
Bootstrap - is loaded when the router boots up and can be upgraded. It then loads the IOS.
IOS - Internetworking Operating System and it is stored in Flash. It can be a chip on the motherboard or a flash card.
startup-config - it is stored in NVRAM.
running-config - it is stored in RAM.
4.2.2) The Internetworking Operating Sysyem

Platform - is the type of hardware the OS runs on.
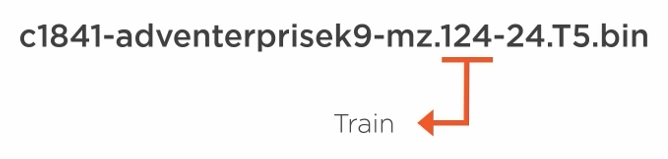
Trains - are the major releases of the OS.
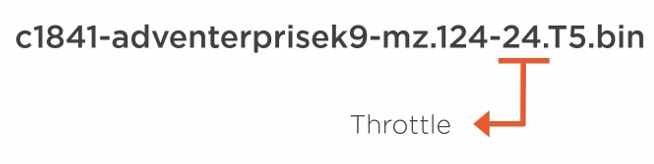
Throttles - are minor releases. which is the numbers in parenthesis.
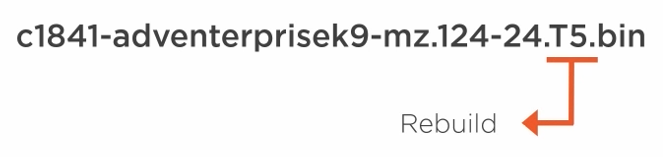
Rebuilds - typically to fix bugs during the process of using the software by Cisco or customers.
The IOS image name follows an specific format.
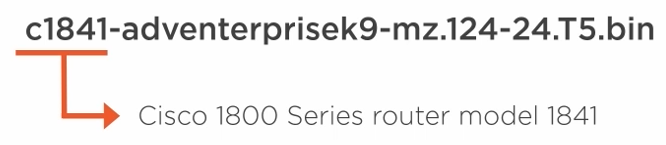
First, it contains the device model.

Second, it describes the feature set in the image.
4.2.3) IOS Licensing
The new image model comes with all the features set in the image. We need to unlock it by buying a license from Cisco.
We buy the license and send the device serial to Cisco's servers which generates a key that we use to unlock the features.

The K9 in the image means it has a cryptographic key to generate keys like for SSH login.
4.3) Router Configuration
4.3.1) Setting up Your Connection to the Router
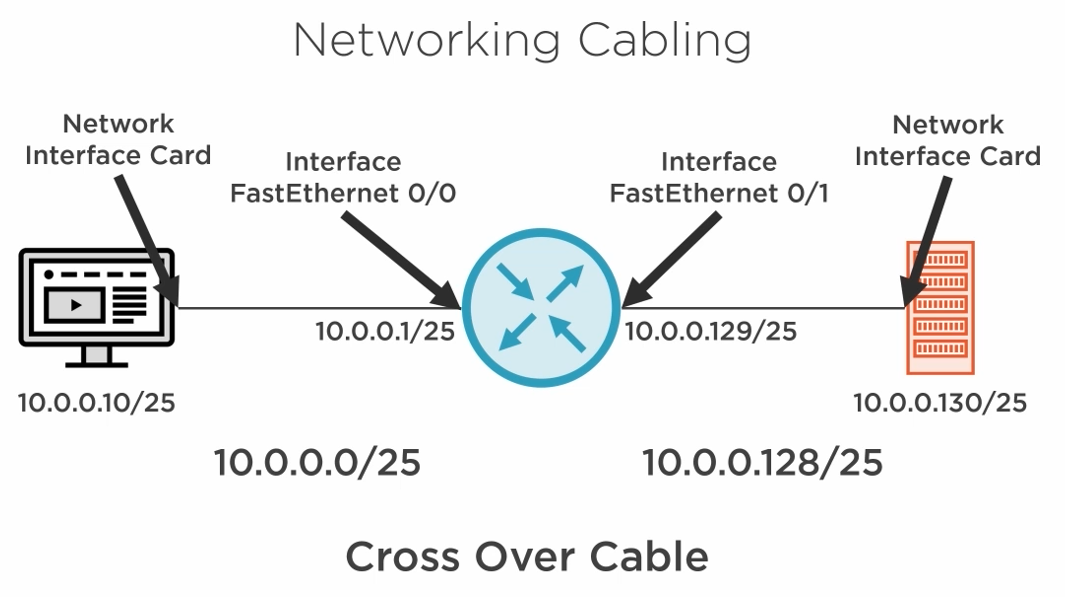
Because we are connecting PCs directly to the router we need to use cross-over cables.
The Cisco CCNA exam considers Auto-MDIX not present on the devices.
Auto MDI/MDIX is a feature that allows network devices to automatically detect the type of Ethernet cable (straight-through or crossover) connected to them and adjust their operation accordingly.
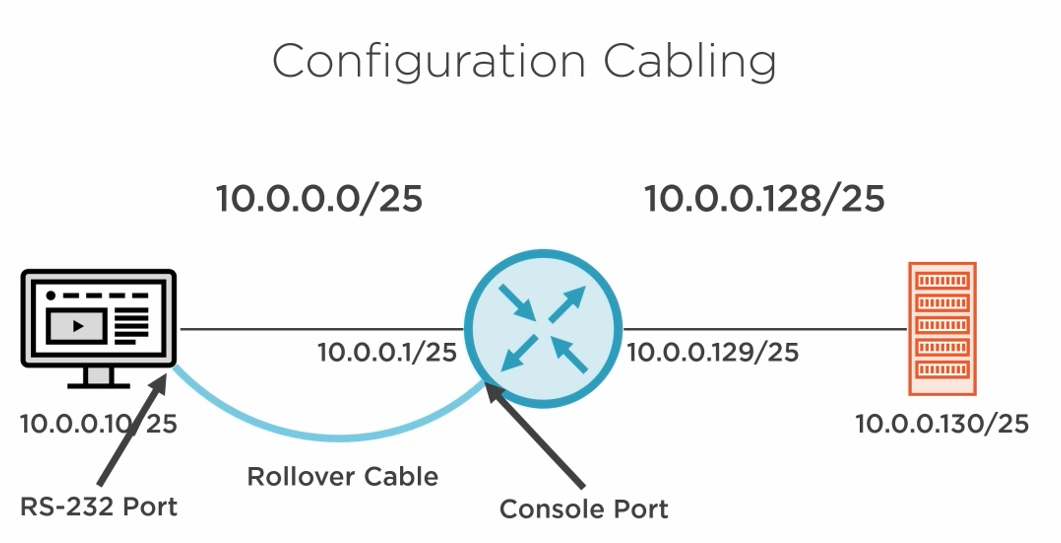
We need a rollover cable to access the router via the console port and configure it since it comes un-configured.
4.3.2) Getting CLI Access
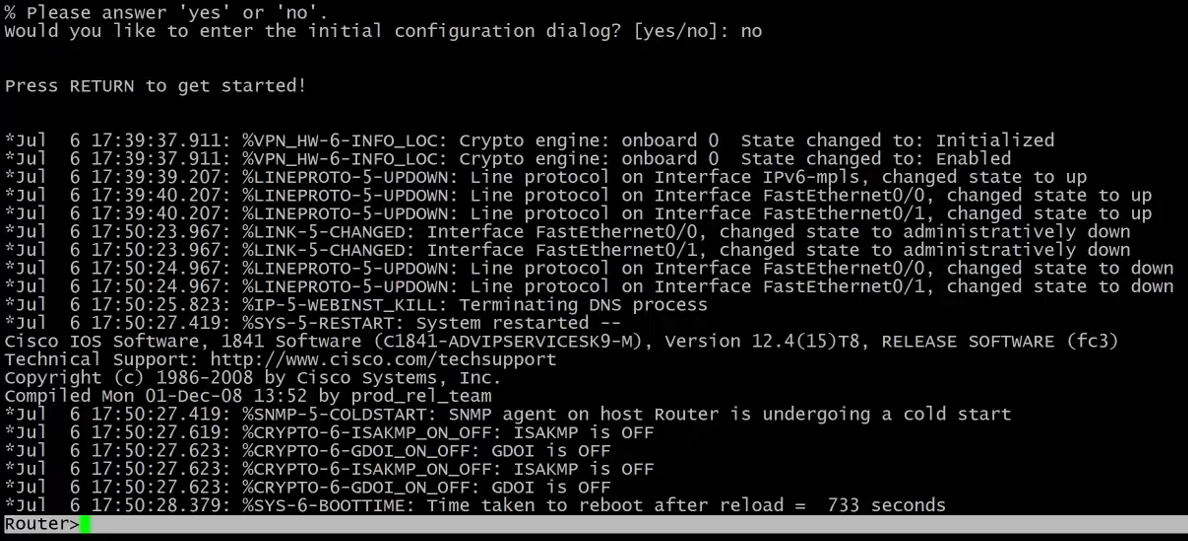
We start by saying no to the configuration dialogue system.
The router starts in user mode and we need to get into privileged mode by typing enable.
Finally, typing configure terminal we are in configuration mode.
4.3.3) Adding Base Config
We can follow the same steps used to configure our switch with the only exception that the IP address can be configured on an interface and not a VLAN.
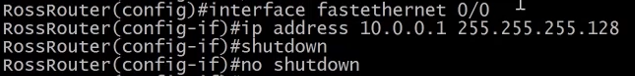
Switch Configuration with SSH 🔗
4.3.4) The Interrupt Boot Process
If we need to go to the BootStrap configuration, we need to interrupt the boot process.
To get into the Bootstrap configuration area, press a key early in the boot process.
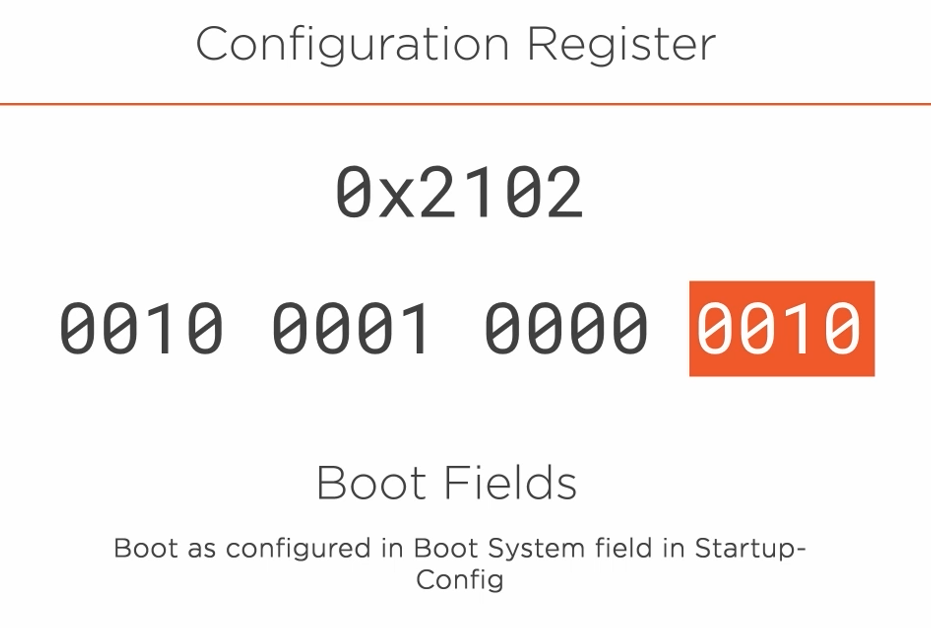
We will have access to the Configuration Register which is a HEX value.
The 16-bit value can be used to configure how the router behaves. When set to 0010 the router will load its configuration from the startup-config file.
It also looks in the configuration for an IOS image to load the operating system and, if not present it will load the first available IOS image.
Below are a few more possible configurations.
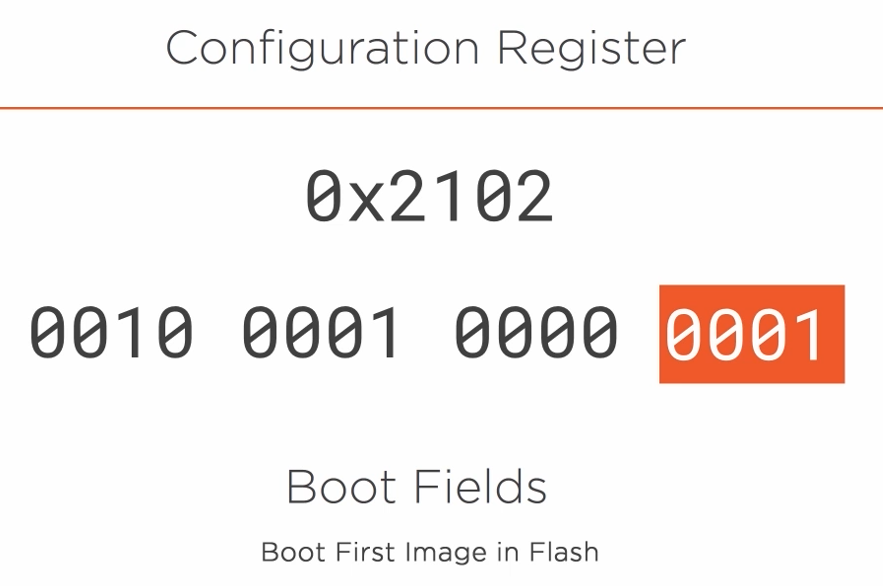
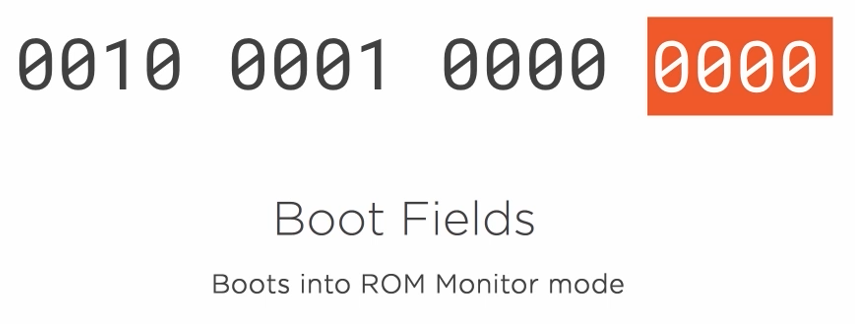
The seventh-bit controls which config file should be loaded.
If set to zero it will load the startup-config.
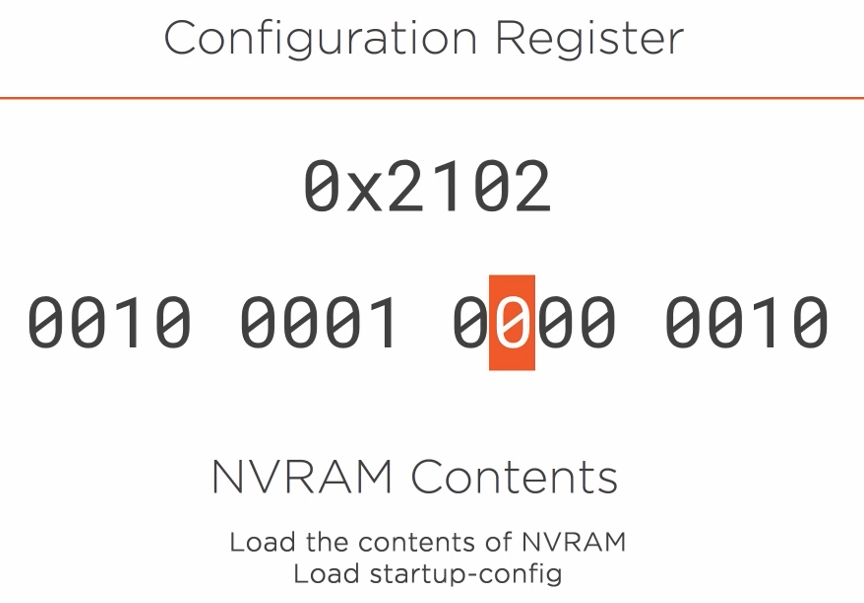
If set to 1 the startup-config will not be loaded. This option can be used to recover the router password.
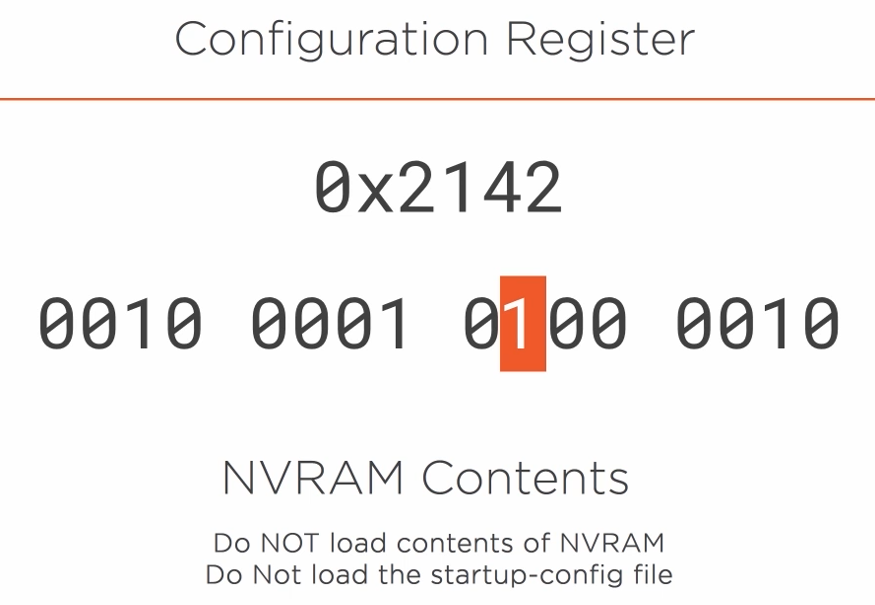
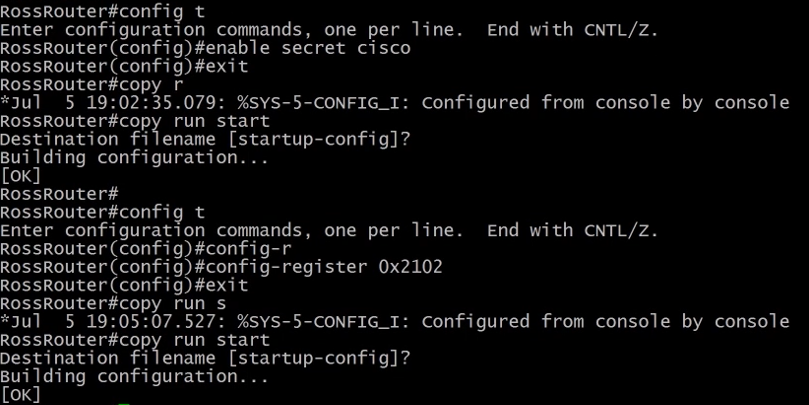
4.3.5) Router Password Reset
Press any key on the keyboard during the early stages of the boot process. You will be in the ronmon mode.
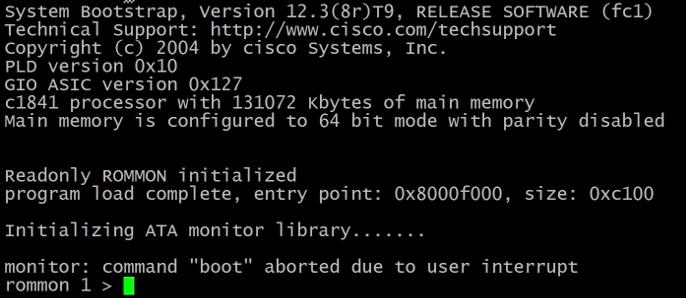
Change the configuration register value to 0x2142 and reboot the router.
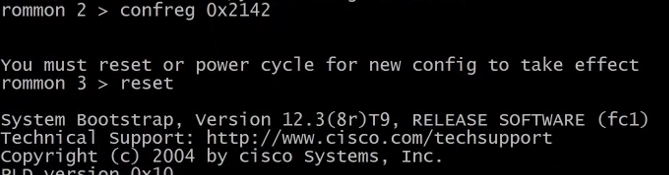
Skip the configuration wizard and go into privileged mode which will not have a password.
Next, copy the startup-config to the running-config and you will still be in privileged mode.
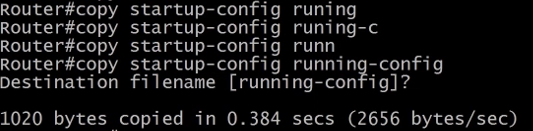
Go into configuration mode and change the router password.
Copy the running-config to the startup-config.
Finally, restore the configuration register to its original value.
4.4) Router Configuration with IPv6
4.4.1) Erasing Startup Config
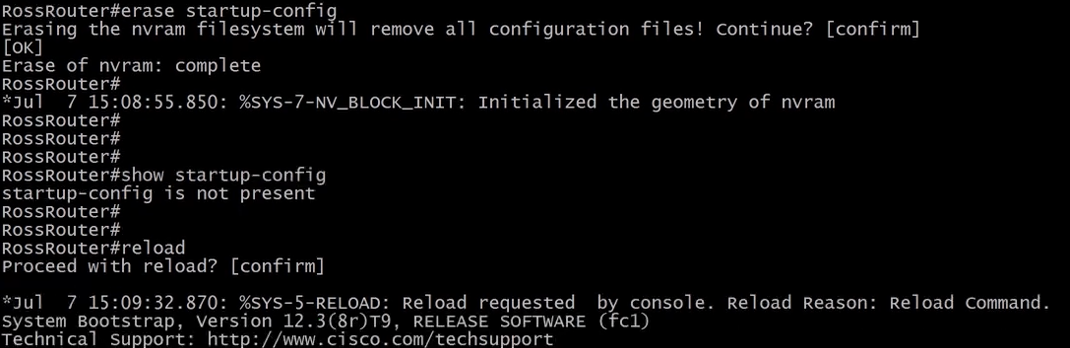
After erasing the startup-config we need to reload the router to delete the running-config.
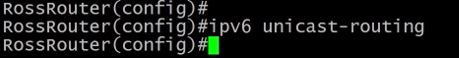
4.4.2) Adding IPv6
1) To enable IPv6 we need to tell the router to enable IPv6 routing.
2) We need to configure IPv6 in our interfaces as shown in the images below.
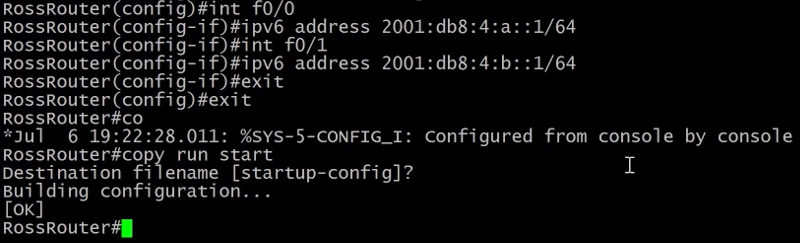
4.5) Upgrading IOS
4.5.1) Why Upgrade The IOS?
We upgrade to change the feature set of the router and fix security fixes.
4.5.2) How to upgrade?
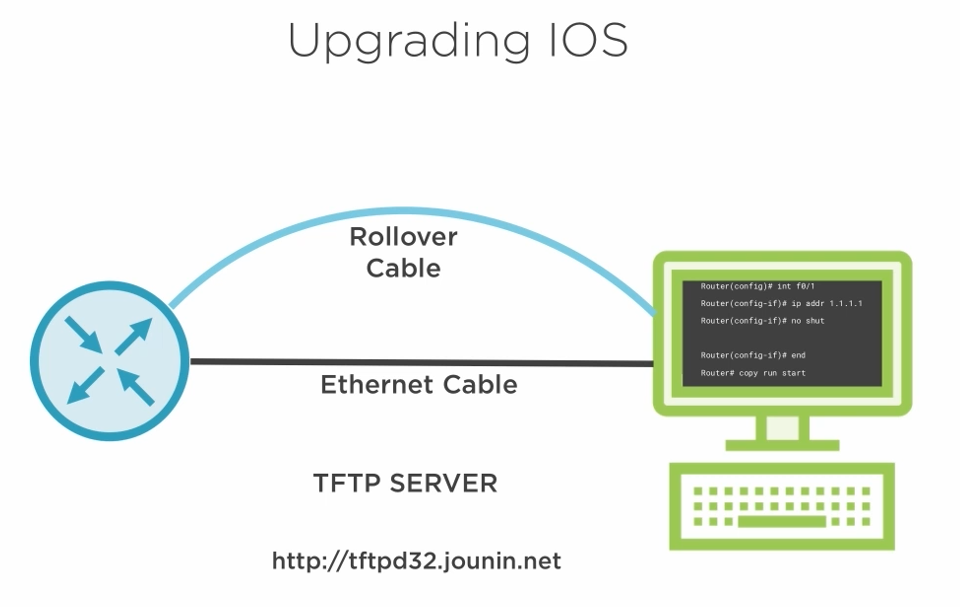
We normally use a rollover cable to access the device through the console and a TFTP server to store the IOS image.
4.5.3) Upgrading IOS
To upgrade the router firmware, we can follow the same steps used to upgrade a Cisco switch IOS. 🔗
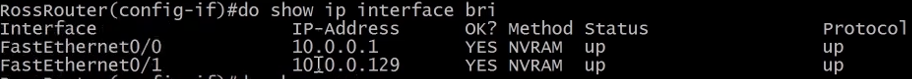
4.5.4) Useful Commands

Use do when in configuration mode to run show commands.
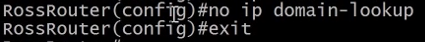
Disable DNS lookups.
5) Routing IPv4 & IPv6
5.1) Address Resolution Protocol
5.1.1) A Basic Network IP Packet
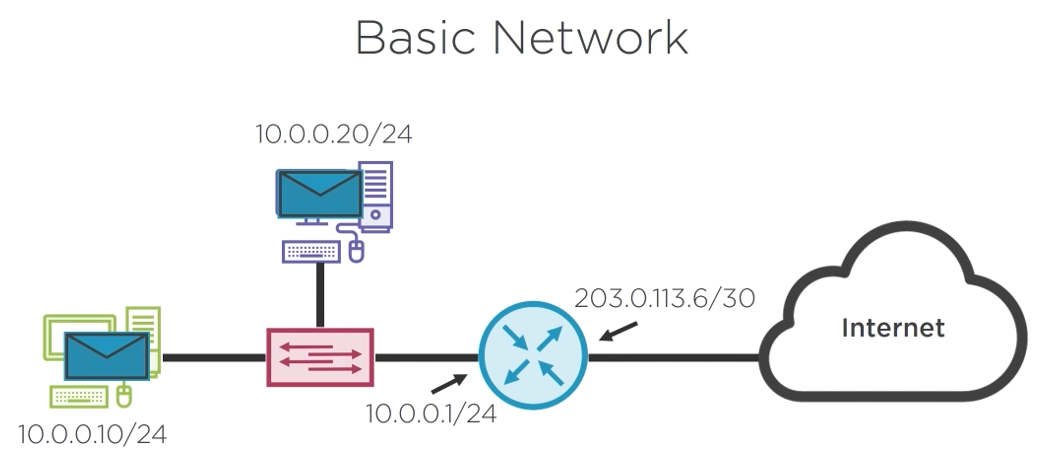
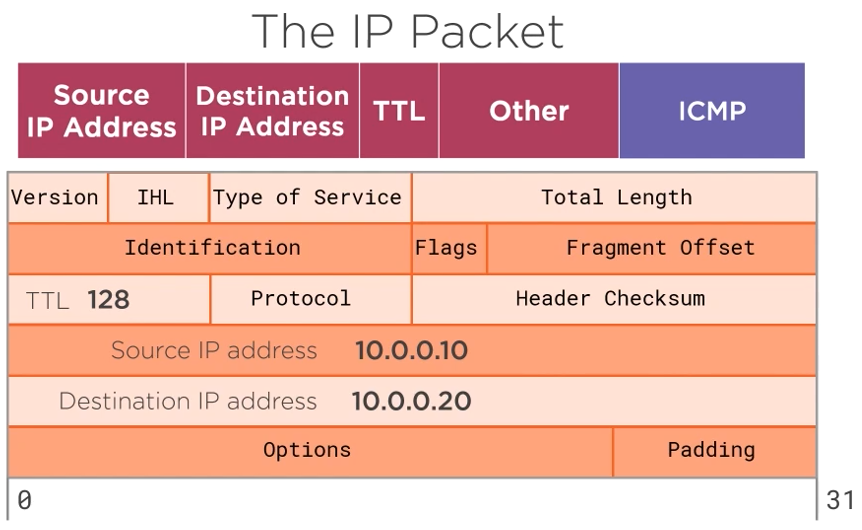
This link contains further explanation on the IP Packet Header Fields. 🔗
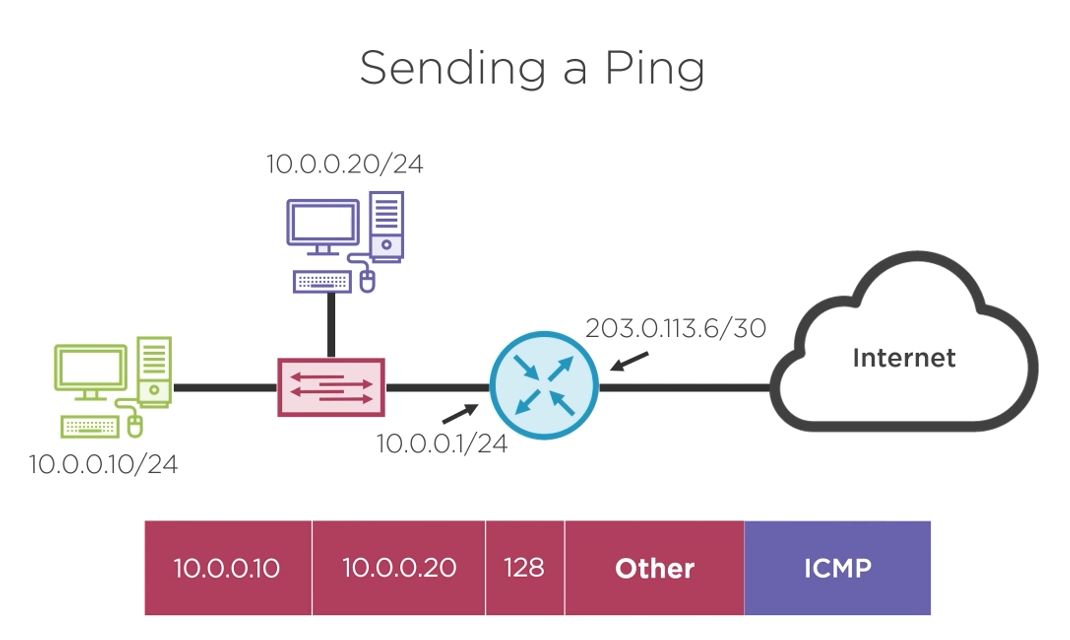
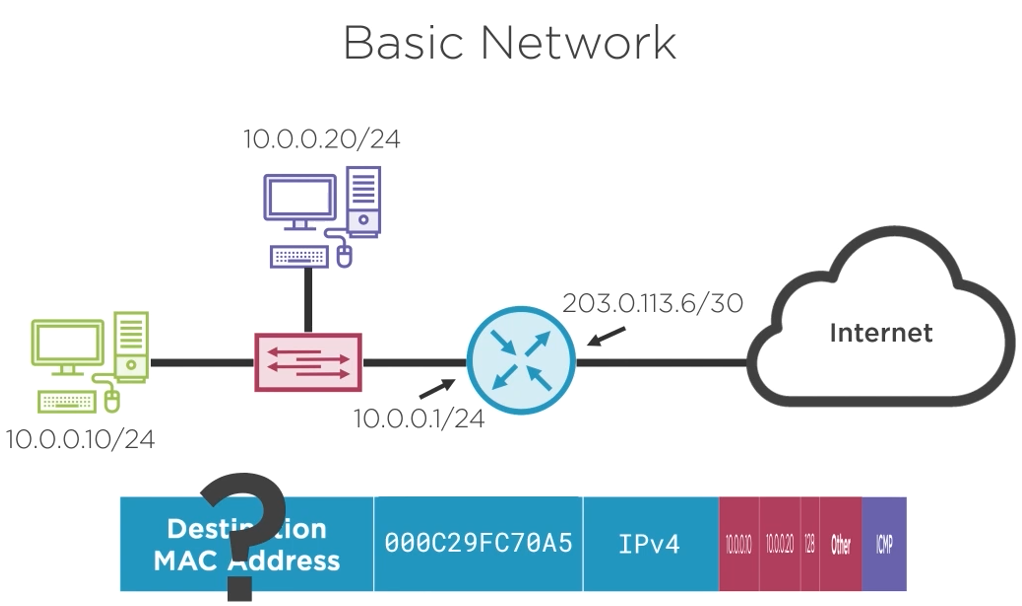
We do not have the destination MAC address to create the frame that will carry our IP Packet. The next topic will explain how to find the destination MAC address.
![Infoitech - [B]logging](https://blog.infoitech.co.uk/content/images/2021/04/youtube-small-cover-1.png)